Ransomware and infostealer threats are evolving faster than most organizations can adapt. While security teams have invested heavily in ransomware resilience, particularly through backup and recovery systems, Picus Security’s Blue Report 2025 shows that today’s most damaging attacks aren’t always about encryption.
Instead, both ransomware operators and infostealer campaigns often focus on credential theft, data exfiltration, and lateral movement, leveraging old-school stealth and persistence to achieve their objectives with minimal disruption.
The evolving adversary tactics are clearly visible when comparing the findings from the Blue Report 2025, based on over 160 million real-world attack simulations, and the Red Report 2025, which analyzes the latest trends in malware, threat actors, and exploitation techniques.
The overlap between the two reports reveals a clear and concerning signal: defenders are falling behind on detecting the very tactics that adversaries now favor the most.
What Is the Blue Report?
The Picus Blue Report is an annual research publication that analyzes how well organizations are preventing and detecting real-world cyber threats.
Unlike traditional reports that focus solely on threat trends or survey data, the Blue Report is based on empirical findings from over 160 million attack simulations conducted across the globe, using the Picus Security Validation Platform.
Now in its third year, the Blue Report provides a data-driven look at the state of enterprise defenses across industries, regions, and attack surfaces.
It evaluates prevention and detection performance against industry-recognized MITRE ATT&CK tactics and techniques, ransomware strains, infostealer behaviors, and newly disclosed vulnerabilities discovered in 2024 and 2025.
By revealing where organizations’ real-world security controls are working and where they’re silently, or not-so-silently, failing, the Blue Report offers security teams a clear path to prioritize high-risk exposures, improve their resilience, and adopt a Continuous Threat Exposure Management (CTEM) strategy backed by Adversarial Exposure Validation (AEV).
Red Flags Confirmed: What the Blue Report Validates from the Red Report
The Red Report 2025 warned of a surge in infostealer malware and the widespread use of encryptionless ransomware attacks. Attackers are no longer relying solely on noisy malware and adversary tactics. Instead, they are quietly stealing sensitive data and using it for blackmail, disruption, or espionage.
Credential-harvesting malware, browser-targeted infostealers, and techniques like Credentials from Password Stores (T1555) were seen in 25% of this year’s malware samples, highlighting a broader pivot toward data theft.
The Blue Report 2025 has now validated these concerns with real-world evidence. In millions and millions of simulated attacks, the findings show the techniques powering modern ransomware and infostealer campaigns are the very ones defenders fail to stop.
-
The data exfiltration prevention rate dropped to just 3%, its lowest level yet, despite the rise of infostealers and double-extortion tactics.
-
Password cracking succeeded in 46% of tested environments, nearly doubling since 2024.
-
Valid Accounts (T1078) had a 98% success rate, confirming how easily attackers exploit stolen or weak credentials to bypass controls.
Together, these gaps illustrate a dangerous truth: adversaries have shifted their methods, but organizations are failing to keep up.
Infostealers Are Booming, Why Are Defenders Lagging Behind?
Infostealers are no longer just opportunistic malware scraping browser passwords from unsuspecting users. They’ve evolved into targeted, persistent tools used in more complex adversary campaigns, designed to stay quiet, remain undetected, and exfiltrate data over long dwell times.
These threats are particularly dangerous because they often succeed without triggering alarms. By using stolen credentials and impersonating legitimate access, they can bypass traditional security controls, blend into normal traffic, and leak sensitive data over days or weeks.
The Blue Report 2025 reinforces just how unprepared most organizations are for this reality. Despite the increase in infostealer usage, data exfiltration prevention remains critically low at 3%.
Most organizations have stronger visibility into what comes in, like malware payloads and phishing attachments, but a much more limited ability to detect what goes out.
Why is this happening? The report showed that a lack of outbound monitoring, insufficient DLP enforcement, and limited behavioral analytics are the key contributors. Attackers are exploiting these gaps to harvest credentials and steal sensitive files, usually without detection.
Why Backup Isn’t a Silver Bullet Against Ransomware
Backup and recovery solutions are essential components of any ransomware response plan, but they are not enough to prevent damage from today’s ransomware campaigns.
As organizations have matured their backup strategies, ransomware groups have responded by changing the rules of the game.
Rather than encrypting data and demanding payment for decryption, they now rely on encryptionless extortion: stealing data, then threatening to leak it publicly. No encryption. No ransom key. Just leverage.
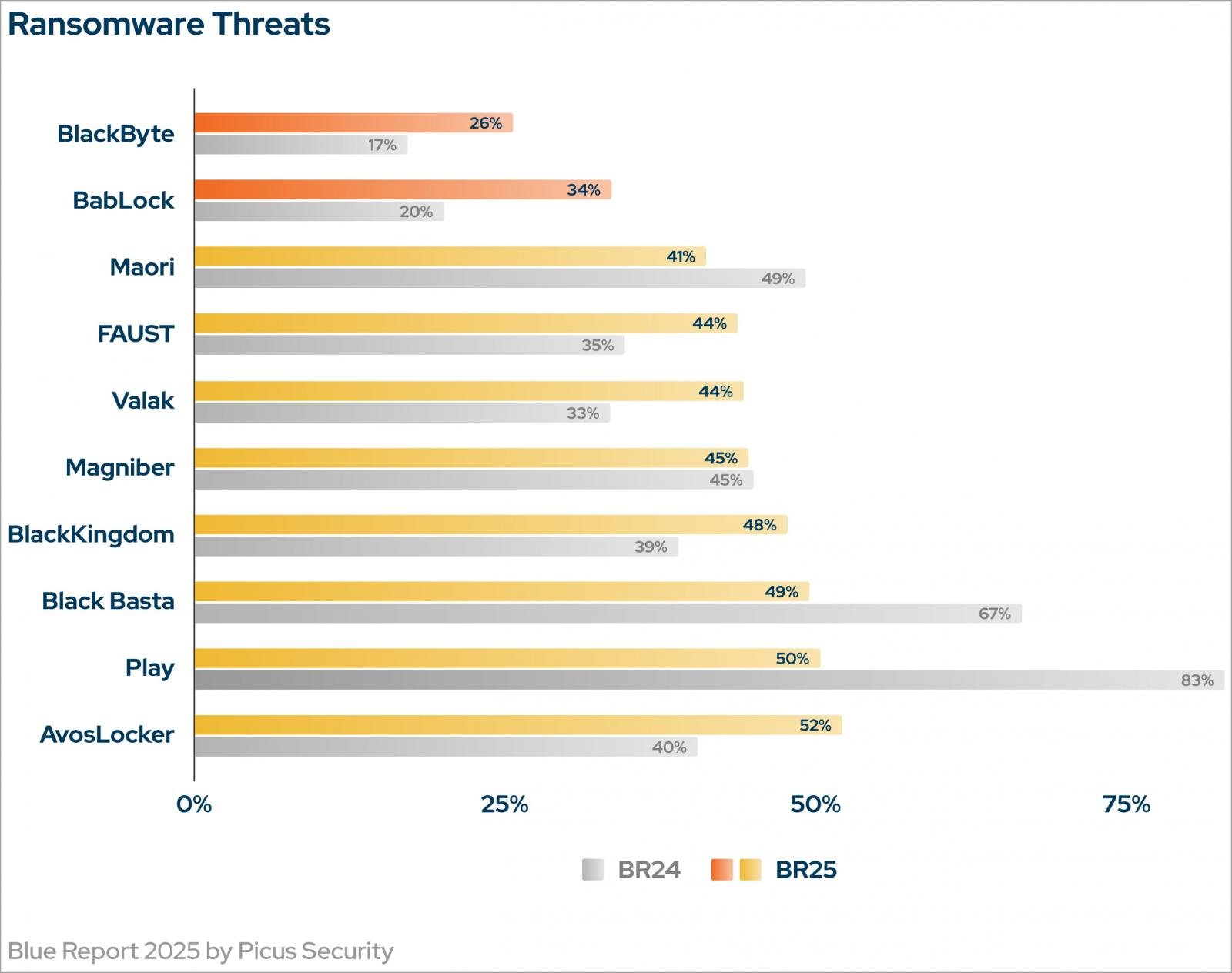
The Blue Report 2025 reflects this evolution. Ransomware variants like BlackByte (26% prevention), BabLock (34% prevention), and Maori (41% prevention) continue to evade controls not because defenders lack recovery strategies, but because other tactics like credential abuse, lateral movement, and exfiltration just aren’t being effectively blocked.
Even if data is backed up and restored, in these instances,the impact is already done once it’s leaked.
That’s why the report emphasizes the need for prevention and detection upstream before data leaves the network, and before credentials are abused to impersonate internal users.
Learn how password cracking nearly doubled, rising from 25% to 46%, revealing critical vulnerabilities. Additionally, prevention rates dropped from 69% to 62% as attacks became more sophisticated.
Find out how to strengthen your security posture and explore the latest insights in threat exposure management with the Picus Blue Report.
Using The Blue Report 2025 to Prioritize The Threats That Matter Most
In a world of competing priorities and limited resources, knowing what to fix first is everything. The Blue Report 2025 helps organizations cut through the staggering amount of noise by analyzing over 160 million attack simulations to reveal the real-world effectiveness of security controls, not in theory, but in practice.
The report provides a comprehensive view of exposure across industries, regions, attack vectors, ransomware families, MITRE ATT&CK tactics and techniques, and recently discovered vulnerabilities.
This level of granularity allows organizations to see exactly where their defenses are underperforming and, more importantly, which gaps present them with the greatest operational risk.
By understanding how their specific business sector or geographic region compares to others, and which attack techniques are most often successful in their sector or region, security teams can prioritize strengthening their defenses based on context, not assumptions.
Whether it’s improving data exfiltration prevention, stopping credential abuse, or tuning detection rules, this year’s new Blue Report offers a clear path forward rooted in real-world adversary behavior.
The report enables defenders to align with Continuous Threat Exposure Management (CTEM), operationalize Adversarial Exposure Validation (AEV), and act decisively on the exposures that matter most.
Ready to Find and Fix Your Most Exploitable Gaps?
The Blue Report 2025 shows how attacker tactics are evolving, and organizations’ defenses are performing against them. Unfortunately, what we’re seeing this year is that infostealers are thriving, ransomware is getting stealthier, and data exfiltration is too often going undetected.
If you’re relying on assumptions, static controls, or outdated detection logic, you’re not seeing anywhere near the full picture.
With Adversarial Exposure Validation, you can go beyond alerts and dashboards to validate what’s actually putting your organization at risk.
See where your defenses are working and where they’re quietly failing. Don’t forget to get your copy today.
Sponsored and written by Picus Security.
