Phishing-as-a-service (PhaaS) platform Tycoon2FA, known for bypassing multi-factor authentication on Microsoft 365 and Gmail accounts, has received updates that improve its stealth and evasion capabilities.
Tycoon2FA was discovered in October 2023 by Sekoia researchers, who later reported significant updates on the phishing kit that increased its sophistication and effectiveness.
Trustwave now reports that the Tycoon 2FA threat actors have added several improvements that bolster the kit’s ability to bypass detection and endpoint security protections.
The first highlighted change is the use of invisible Unicode characters to hide binary data within JavaScript, as first reported by Juniper Threat Labs in February. This tactic allows the payload to be decoded and executed as normal at runtime while evading manual (human) and static pattern-matching analysis.
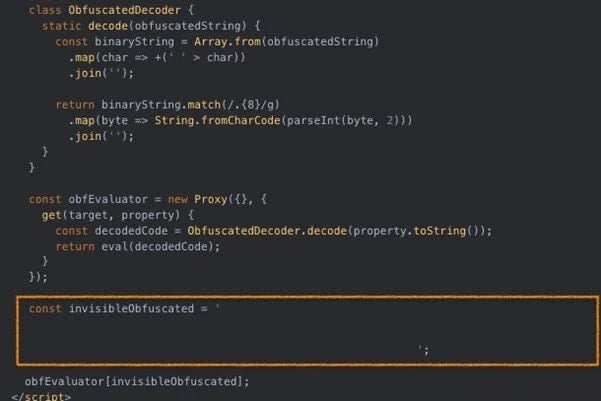
Source: Trustwave
The second development is the switch from Cloudflare Turnstile to a self-hosted CAPTCHA rendered via HTML5 canvas with randomized elements.
Likely, the creators of Tycoon 2FA opted for this change to evade fingerprinting and flagging by domain reputation systems and gain better customization control over the page’s content.
The third major change is the inclusion of anti-debugging JavaScript that detects browser automation tools like PhantomJS and Burp Suite and blocks certain actions associated with analysis.
When suspicious activity is detected or the CAPTCHA fails (potential indication of security bots), the user is served a decoy page or is redirected to a legitimate website like rakuten.com.
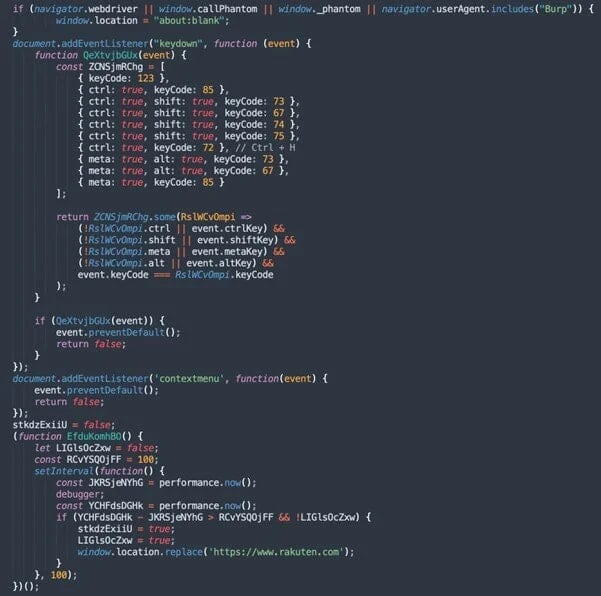
Source: Trustwave
Trustwave underlines that while these evasion techniques aren’t novel individually, they make a big difference when combined, complicating detection and analysis that can uncover phishing infrastructure and lead to takedowns and disruption.
SVG lures surging
In a separate but related report, Trustwave says it has identified a dramatic increase in phishing attacks using malicious SVG (Scalable Vector Graphics) files, driven by PhaaS platforms like Tycoon2FA, Mamba2FA, and Sneaky2FA.
The cybersecurity firm reports a steep rise of 1,800% from April 2024 to March 2025, indicating a clear shift in tactics favoring the particular file format.
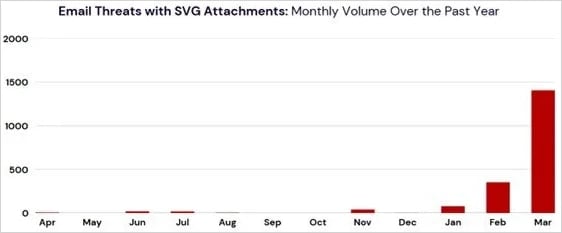
Source: Trustwave
The Malicious SVGs used in the phishing attacks are for images disguised as voice messages, logos, or cloud document icons. However, SVG files can also contain JavaScript, which is automatically triggered when the image is rendered in browsers.
This code is obfuscated using base64 encoding, ROT13, XOR encryption, and junk code, so detection is less likely.
The function of the malicious code is to redirect the message recipients to Microsoft 365 phishing pages that steal their account credentials.
A case study presented in the Trustwave report concerns a fake Microsoft Teams voicemail alert with an SVG file attachment disguised as an audio message. Clicking it opens an external browser that executes JavaScript, redirecting to a fake Office 365 login page.
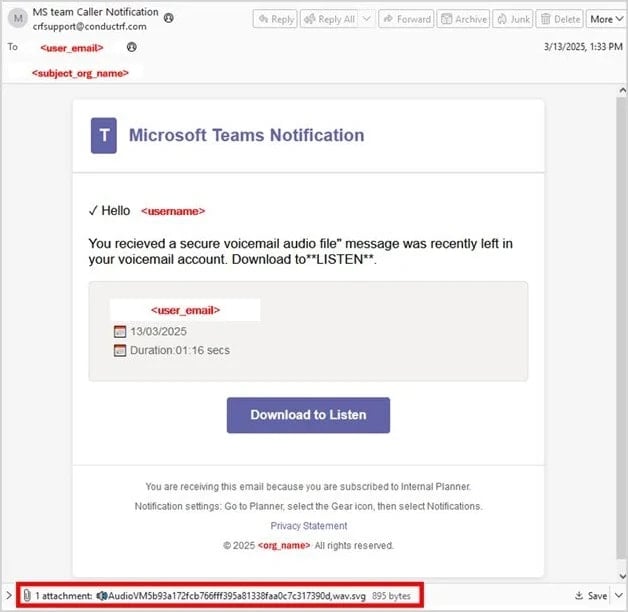
Source: Trustwave
The rise of PhaaS platforms and SVG-based phishing calls for heightened vigilance and the need for sender authenticity verification.
An effective defense measure is to block or flag SVG attachments in email gateways and use phishing-resistant MFA methods like FIDO-2 devices.
