Still getting login codes via text or authenticator apps? You’re not alone—and that’s a big problem. What used to feel like a smart security layer is now one of the easiest ways for attackers to gain access to your accounts.
First we were told to use SMS for MFA. Then we were told: “Don’t use SMS for MFA, use an authenticator app instead.”
And while that may seem like a step forward, it’s still fundamentally flawed. Authenticator apps do improve over SMS by avoiding message interception, but they are easily fished (every day now) and often rely on time-based codes that can also be phished, relayed, or even intercepted if the device is compromised.
The core issue remains: the system has no idea whether it’s being used on the legitimate site or a perfect fake. So while it’s a different system, it’s not a secure one—just a broken version of the same problem.
Want proof? Recent high-profile breaches (Including Aflac, Erie Insurance and Philadelphia Insurance Companies) showed exactly how easy this is.
Some were calls to IT help desks asking for an MFA bypass or reset. But the favorite is quickly becoming a phishing/spoof trick.
A phishing email lands. The user clicks. The spoofed website is pixel perfect. They enter their username, password, and they confirm it’s them on their auth app. Done. The attacker is in.
Because the authenticator app doesn’t verify who is asking or where the request came from – you become the attack vector.
Download to explore how ransomware attacks are evolving and why legacy MFA can’t keep up.
This guide reveals the real-world impact of phishing-resistant MFA, how it stops ransomware before damage is done, and why CISOs are switching to next-generation authentication.
This is what no one wants to say out loud: authenticator apps and SMS codes can be phished in real time. They give users a false sense of security while offering little to no actual protection against the most common threat today—spoofed websites paired with social engineering.
Even major platforms like Amazon and Google, according to recent investigations, use third-party SMS delivery firms—some with ties to surveillance operations. These intermediaries have already been linked to security breaches. Even the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a blunt warning: “Do not use SMS as a second factor.”
So you might think passkeys are an answer—and they are a small step forward but now are easily compromised as well. They cryptographically bind login credentials to websites and reduce human error. But they’re not foolproof. Passkeys are often stored and synced via cloud accounts.
If someone hijacks your Apple or Google account, they can gain access to every passkey you’ve saved. A stolen or compromised phone? Same risk. And malware or user coercion can still result in approvals that give attackers full access.
So what is the solution? It’s time to move past the illusion of codes and cloud-sync. Enter Token Ring and Token BioStick—purpose-built, biometric hardware authenticators that completely remove the weak links.
Here’s why they work:
- No cloud.
- No shared secrets.
- No reliance on user judgment.
- No code entry.
Token Ring and Token BioStick store your credentials inside tamper-proof secure elements. They only authenticate when your fingerprint matches, you’re physically present, and the domain requesting access is verified cryptographically.
Even if an attacker steals the device, it’s useless without your fingerprint. Even if you’re tricked into visiting a fake site, it won’t even come alive let alone authenticate—because the device must be in proximity to the device logging in, and even if someone figured that out, the cryptographic handshake fails automatically.
They cannot be phished. They cannot be hijacked remotely. They eliminate trust from the equation. That’s the power of biometric FIDO2 done right, in secure hardware, with no shortcuts.
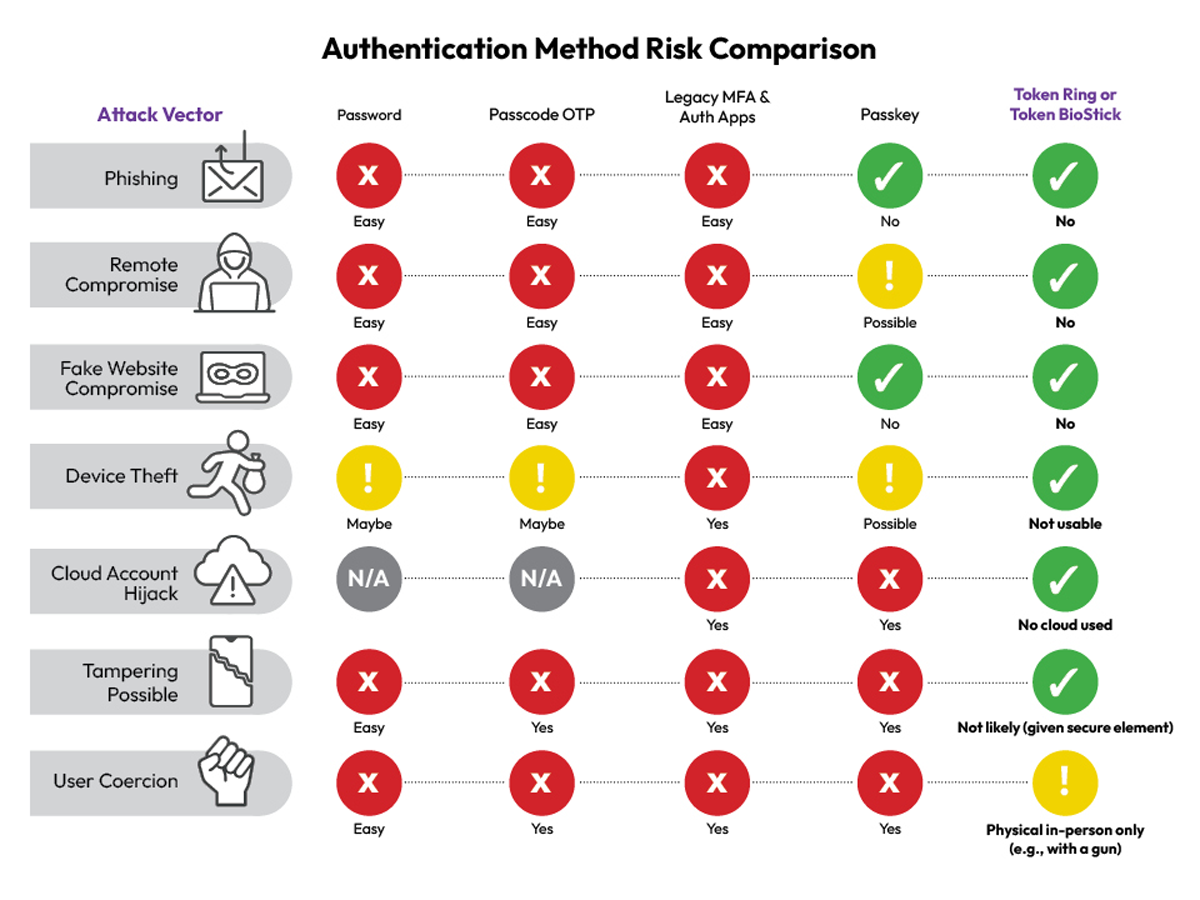
Bottom line: If your MFA can be tricked by a fake website, it’s already obsolete.
SMS is dead. Auth apps are legacy. Passkeys are progress—but flawed.
Token Ring and Token BioStick are the gold standard. Phishing-proof. Tamper-resistant. Biometrically bound. Proximity required.
Attackers are coming for your MFA and auth apps—it’s not a matter of if, but when. And every other method today? They fail.
It’s time to upgrade. Before you’re the next headline.
Sponsored and written by Token.
