How EDRSilencer Works
The latest version of EDRSilencer detects and blocks up to 16 modern EDR tools, including:
- Microsoft Defender
- SentinelOne
- FortiEDR
- Palo Alto Networks Traps/Cortex XDR
- Cisco Secure Endpoint
- ElasticEDR
- Carbon Black EDR
- TrendMicro Apex One
The tool works by setting persistent filters in WFP, which is commonly used by security products like firewalls and antivirus solutions. These custom rules allow attackers to intercept and block the network traffic that would otherwise alert the EDR management server to suspicious activities.
Blocking the traffic of hardcoded executables
Source: Trend Micro
By blocking telemetry data and security alerts, EDRSilencer enables attackers to conduct unauthorized activities—such as deploying malware, escalating privileges, or exfiltrating data—without raising alarms. This capability makes it a powerful tool in advanced persistent threat (APT) campaigns and financially motivated cyberattacks.
Customizing EDRSilencer for Specific Attacks
In addition to its hardcoded list of 16 EDR tools, EDRSilencer allows attackers to customize its behavior by adding filters for specific processes or EDR components. By providing the file paths of additional security tools, attackers can expand the list of targets beyond those included by default. This customization ensures that even partially blocked EDR solutions can be fully neutralized in targeted attacks.
Trend Micro‘s testing has shown that, when used in this way, EDRSilencer can effectively stop security tools from sending logs or alerts, confirming its ability to bypass detection in even the most secure environments.
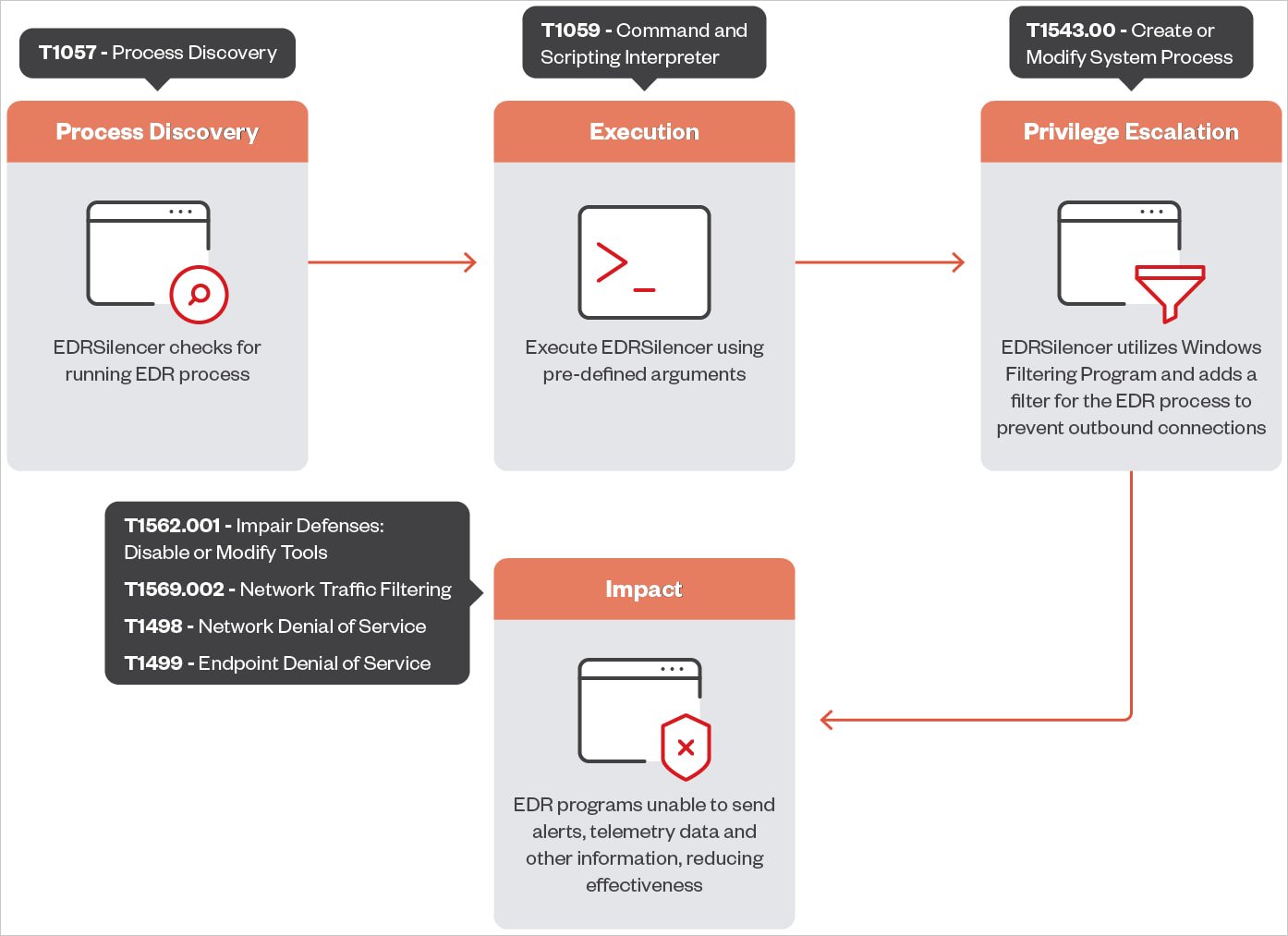 EDRSilencer attack chain
EDRSilencer attack chain
Source: Trend Micro