Covert Audio Channel Exploitation
PIXHELL was developed by Dr. Mordechai Guri from Ben-Gurion University of the Negev, known for his research into data exfiltration from air-gapped systems. The method capitalizes on unintended acoustic emissions from LCD screens, caused by coil whine, capacitor noise, or intrinsic vibrations.
Attackers can use malware to encode data into the acoustic signals using modulation schemes such as:
- On-Off Keying (OOK): Data is encoded by turning sound on and off.
- Frequency Shift Keying (FSK): Data is encoded by switching between frequencies.
- Amplitude Shift Keying (ASK): Data is encoded by altering the sound’s amplitude (volume).
Modulating acoustic signals at various frequences
Source: Arxiv.org
These signals are transmitted through the LCD screen by changing pixel patterns, which generates the necessary sound. A nearby microphone-equipped device can capture these signals for later transmission to an attacker for decoding.
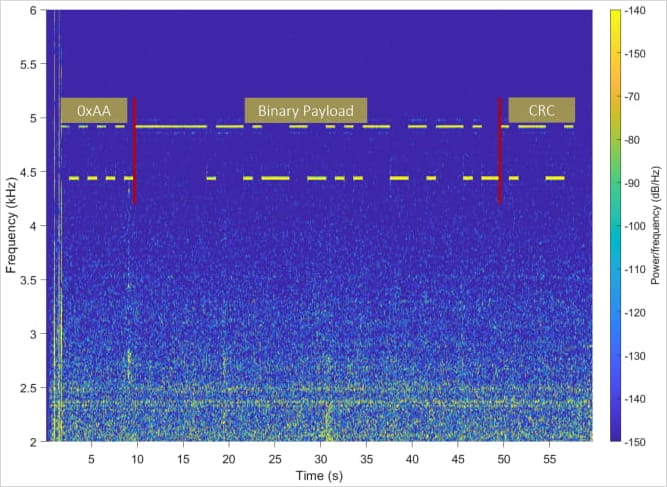 Spectrogram of acoustic signal received by a nearby microphone
Spectrogram of acoustic signal received by a nearby microphone
Source: Arxiv.org
Stealthy and Efficient
The frequencies used in PIXHELL attacks are typically in the 0-22 kHz range, which is mostly inaudible to humans. At the same time, the pixel patterns used in the attack are low-brightness or invisible to the user, making the attack extremely stealthy.
In a setting with multiple infected air-gapped systems, PIXHELL can exfiltrate data from all of them simultaneously.