Palo Alto Networks warns that a file read vulnerability (CVE-2025-0111) is now being chained in attacks with two other flaws (CVE-2025-0108 with CVE-2024-9474) to breach PAN-OS firewalls in active attacks.
The vendor first disclosed the authentication bypass vulnerability tracked as CVE-2025-0108 on February 12, 2025, releasing patches to fix the vulnerability. That same day, Assetnote researchers published a proof-of-concept exploit demonstrating how CVE-2025-0108 and CVE-2024-9474 could be chained together to gain root privileges on unpatched PAN-OS firewalls.
A day later, network threat intel firm GreyNoise reported that threat actors had begun actively exploiting the flaws, with attempts coming from two IP addresses.
CVE-2024-9474 is a privilege escalation flaw in PAN-OS fixed in November 2024 that allows a PAN-OS administrator to execute commands on firewalls with root privileges. Palo Alto Networks warned at the disclosure that the vulnerability was exploited as a zero-day.
CVE-2025-0111 is a file read vulnerability in PAN-OS, allowing authenticated attackers with network access to the management web interface to read files that are readable by the “nobody” user.
The CVE-2025-0111 flaw was also fixed on February 12, 2025, but the vendor updated its bulletin today to warn that it is also now being used in an exploit chain with the other two vulnerabilities in active attacks.
“Palo Alto Networks has observed exploit attempts chaining CVE-2025-0108 with CVE-2024-9474 and CVE-2025-0111 on unpatched and unsecured PAN-OS web management interfaces,” reads the updated bulletin.
While Palo Alto Networks has not shared how the exploit chain is being abused, BleepingComputer has been told they could be chained together to download configuration files and other sensitive information.
Exploitation activity increases
Not only has the scope broadened, but an update on GreyNoise’s bulletin indicates that the exploitation activity has also increased pace.
GreyNoise reports now seeing 25 IP addresses targeting CVE-2025-0108, whereas its initial report from February 13 only logged two.
The top sources of the attacks are the United States, Germany, and the Netherlands, although this does not mean the attackers are actually based in those locations.
Macnica researcher Yutaka Sejiyama told BleepingComputer that his scans returned thousands of PAN-OS devices that expose their web management interface to the internet.
“For the newly patched CVE-2025-0108 and CVE-2025-0111, the majority of servers that publicly expose their web management interface are still unpatched,” Sejiyama told BleepingComputer.
“Out of 3,490 servers facing the internet, only a few dozen have applied the patch.”
Of these exposed devices, 1,168 have not patched CVE-2025-0108 and CVE-2025-0111 but have patched CVE-2024-9474.
The researcher said that when considering all three flaws chained in the attacks, 65% (2,262 devices) remain vulnerable to at least one of them.
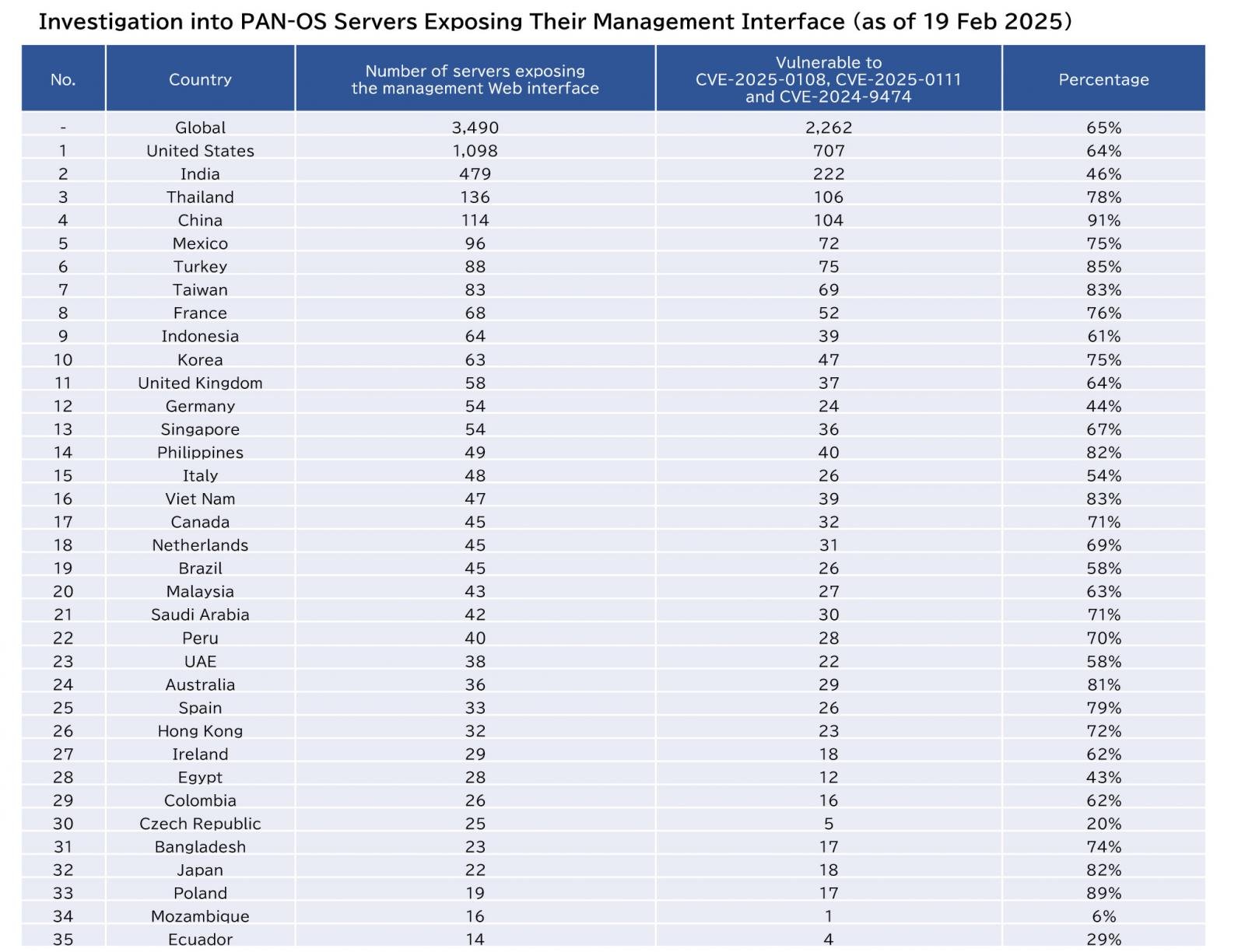
Source: Sejiyama
Amidst this situation and active exploitation, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) has added CVE-2025-0108 to its ‘Known Exploited Vulnerabilities’ (KEV) catalog.
The organization has given federal agencies until March 11, 2025, to apply the available updates/mitigations or stop using the product.