Over 1,200 internet-exposed SAP NetWeaver instances are vulnerable to an actively exploited maximum severity unauthenticated file upload vulnerability that allows attackers to hijack servers.
SAP NetWeaver is an application server and development platform that runs and connects SAP and non-SAP applications across different technologies.
Last week, SAP disclosed an unauthenticated file upload vulnerability, tracked as CVE-2025-31324, in SAP NetWeaver Visual Composer, specifically the Metadata Uploader component.
The flaw allows remote attackers to upload arbitrary executable files on exposed instances without authenticating, achieving code execution and full system compromise.
Multiple cybersecurity firms, including ReliaQuest, watchTowr, and Onapsis, confirmed the flaw is actively exploited in attacks, with threat actors utilizing it to drop web shells on vulnerable servers.
A SAP spokesperson told BleepingComputer that they were aware of these attempts and released a workaround on April 8, 2024, followed by a security update that addressed CVE-2025-31324 on April 25.
SAP told BleepingComputer that they are not aware of any cases where these attacks impacted customer data or systems.
Widely exploited in attacks
Researchers have now confirmed that many vulnerable SAP Netweaver servers are exposed on the internet, making them prime targets for attacks.
The Shadowserver Foundation found the 427 exposed servers, warning of the massive exposed attack surface and the potentially severe repercussions of exploitation.
Most of the vulnerable systems (149) are in the United States, followed by India (50), Australia (37), China (31), Germany (30), the Netherlands (13), Brazil (10), and France (10).
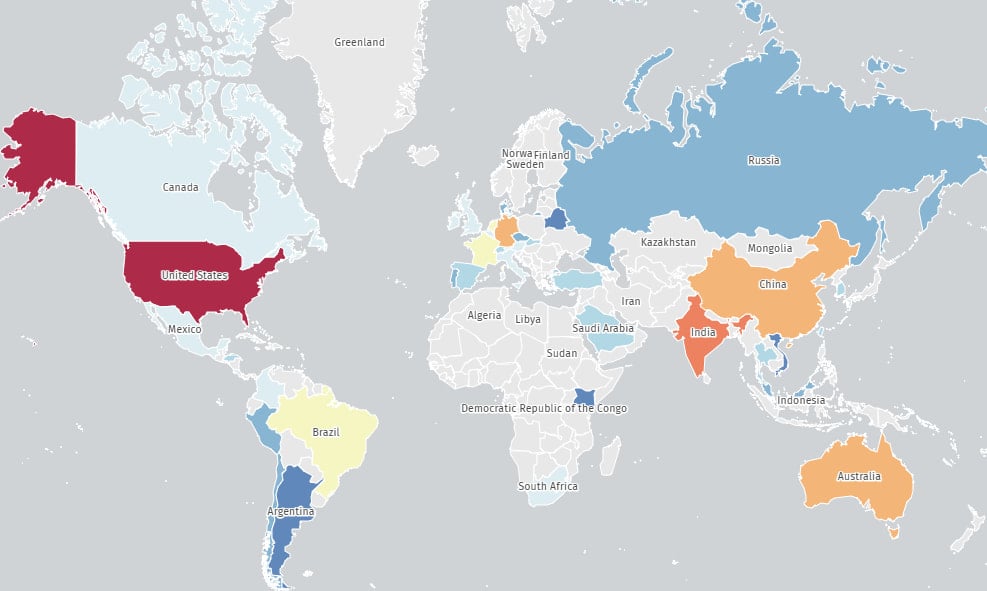
Source: The Shadowserver Foundation
However, cyber defense search engine Onyphe paints a more dire picture, telling BleepingComputer that there are 1,284 vulnerable servers exposed online, with 474 already having been compromised with webshells.
“Something like 20 Fortune 500/Global 500 companies are vulnerable, and many of them are compromised,” Onyphe CTO Patrice Auffret told BleepingComputer.
Researchers reported that the threat actors are utilizing webshells with names like, “cache.jsp” and “helper.jsp.” Howver, Nextron Research says they are also using random names, making it more difficult to find vulnerable Netweaver instances.
While the number of servers is not massive, the risk is still significant, given that large enterprises and multinational corporations commonly use SAP NetWeaver.
To address the risk, it is recommended that the latest security update be applied by following the vendor’s instructions in this bulletin.
If unable to apply the update, the below mitigations are recommended:
- Restrict access to the /developmentserver/metadatauploader endpoint.
- If Visual Composer is not in use, consider turning it off entirely.
- Forward logs to SIEM and scan for unauthorized files in the servlet path.
RedRays has also released a scanner tool for CVE-2025-31324 that can help pinpoint risks in large environments.
BleepingComputer contacted SAP with further questions about the active exploitation and will update the story with any response.