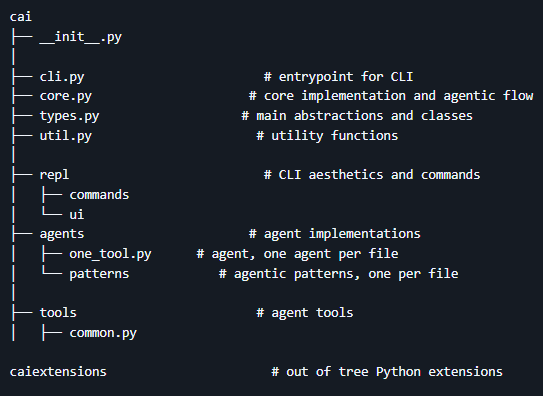
Architecture
CAI focuses on making cybersecurity agent coordination and execution lightweight, highly controllable, and useful for humans. To do so it builds upon 7 pillars: Agents, Tools, Handoffs, Patterns, Turns, Tracing and HITL.
If you want to dive deeper into the code, check the following files as a start point for using CAI:
Agent
At its core, CAI abstracts its cybersecurity behavior via Agents and agentic Patterns. An Agent in an intelligent system that interacts with some environment. More technically, within CAI we embrace a robotics-centric definition wherein an agent is anything that can be viewed as a system perceiving its environment through sensors, reasoning about its goals and and acting accordingly upon that environment through actuators (adapted from Russel & Norvig, AI: A Modern Approach). In cybersecurity, an Agent interacts with systems and networks, using peripherals and network interfaces as sensors, reasons accordingly and then executes network actions as if actuators. Correspondingly, in CAI, Agents implement the ReACT (Reasoning and Action) agent model.
from cai.sdk.agents import Agent from cai.core import CAI ctf_agent = Agent( name="CTF Agent", instructions="""You are a Cybersecurity expert Leader""", model= "gpt-4o", ) messages = [ "role": "user", "content": "CTF challenge: TryMyNetwork. Target IP: 192.168.1.1" ] client = CAI() response = client.run(agent=ctf_agent, messages=messages)
Tools
Tools let cybersecurity agents take actions by providing interfaces to execute system commands, run security scans, analyze vulnerabilities, and interact with target systems and APIs – they are the core capabilities that enable CAI agents to perform security tasks effectively; in CAI, tools include built-in cybersecurity utilities (like LinuxCmd for command execution, WebSearch for OSINT gathering, Code for dynamic script execution, and SSHTunnel for secure remote access), function calling mechanisms that allow integration of any Python function as a security tool, and agent-as-tool functionality that enables specialized security agents (such as reconnaissance or exploit agents) to be used by other agents, creating powerful collaborative security workflows without requiring formal handoffs between agents.
from cai.sdk.agents import Agent from cai.tools.common import run_command from cai.core import CAI def listing_tool(): """ This is a tool used list the files in the current directory """ command = "ls -la" return run_command(command, ctf=ctf) def generic_linux_command(command: str = "", args: str = "", ctf=None) -> str: """ Tool to send a linux command. """ command = f'command args' return run_command(command, ctf=ctf) ctf_agent = Agent( name="CTF Agent", instructions="""You are a Cybersecurity expert Leader""", model= "claude-3-7-sonnet-20250219", functions=[listing_tool, generic_linux_command]) client = CAI() messages = [ "role": "user", "content": "CTF challenge: TryMyNetwork. Target IP: 192.168.1.1" ] response = client.run(agent=ctf_agent, messages=messages)
You may find different tools. They are grouped in 6 major categories inspired by the security kill chain:
- Reconnaissance and weaponization – reconnaissance (crypto, listing, etc)
- Exploitation – exploitation
- Privilege escalation – escalation
- Lateral movement – lateral
- Data exfiltration – exfiltration
- Command and control – control
Handoffs
Handoffs allow an Agent to delegate tasks to another agent, which is crucial in cybersecurity operations where specialized expertise is needed for different phases of an engagement. In our framework, Handoffs are implemented as tools for the LLM, where a handoff/transfer function like transfer_to_flag_discriminator enables the ctf_agent to pass control to the flag_discriminator_agent once it believes it has found the flag. This creates a security validation chain where the first agent handles exploitation and flag discovery, while the second agent specializes in flag verification, ensuring proper segregation of duties and leveraging specialized capabilities of different models for distinct security tasks.
from cai.sdk.agents import Agent
from cai.core import CAI
ctf_agent = Agent(
name="CTF Agent",
instructions="""You are a Cybersecurity expert Leader""",
model= "deepseek/deepseek-chat",
functions=[],
)
flag_discriminator_agent = Agent(
name="Flag Discriminator Agent",
instructions="You are a Cybersecurity expert facing a CTF challenge. You are in charge of checking if the flag is correct.",
model= "qwen2.5:14b",
functions=[],
)
def transfer_to_flag_discriminator():
"""
Transfer the flag to the flag_discriminator_agent to check if it is the correct flag
"""
return flag_discriminator_agent
ctf_agent.functions.append(transfer_to_flag_discriminator)
client = CAI()
messages = [
"role": "user",
"content": "CTF challenge: TryMyNetwork. Target IP: 192.168.1.1"
]
response = client.run(agent=ctf_agent,
messages=messages)