Mandiant researchers have unveiled a novel method to bypass browser isolation technology, using QR codes to enable command-and-control (C2) operations.
What Is Browser Isolation?
Browser isolation is a widely adopted security technology designed to prevent malicious code from reaching local systems. By routing all local web browser requests through remote browsers hosted in cloud environments or virtual machines:
- Scripts and content are executed remotely.
- Only the rendered pixel stream of the webpage is sent back to the local browser, ensuring malicious content cannot directly affect the user’s device.
This effectively blocks many C2 communication models, which often rely on HTTP traffic, by filtering out malicious scripts and commands.
Overview of browser isolation
Source: Mandiant
Mandiant’s QR Code-Based Bypass
Mandiant’s researchers have developed a proof-of-concept (PoC) demonstrating how QR codes can bypass browser isolation protections.
Instead of embedding malicious commands in HTTP traffic, attackers encode them into QR codes displayed on the webpage. Because browser isolation streams visual content, the QR codes remain intact when rendered and are sent back to the client.
How It Works:
- QR Code Delivery: Commands are encoded as QR codes on the malicious webpage.
- Local Retrieval: A headless browser or malware already infecting the target device captures and decodes the QR codes.
- Execution: The decoded commands are used for C2 operations, enabling remote attackers to issue commands or exfiltrate data.
Mandiant integrated the attack with Cobalt Strike’s External C2 feature, a well-known penetration testing framework often exploited by attackers.
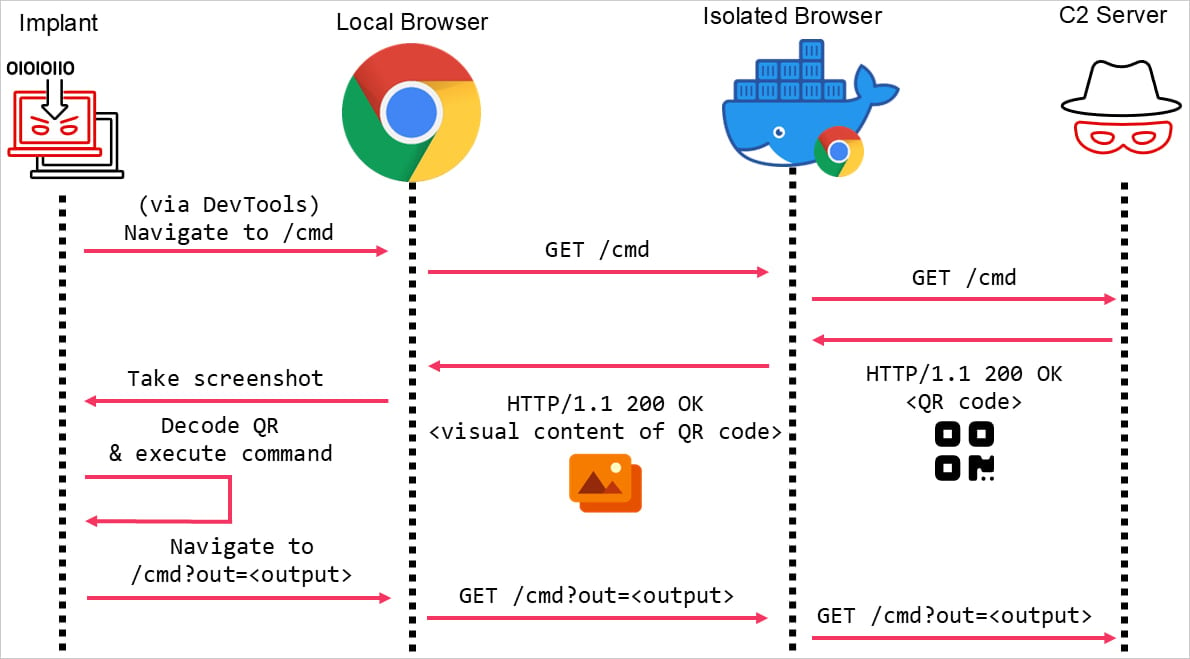 Bypassing browser isolation using a QR code
Bypassing browser isolation using a QR code
Source: Mandiant