Ymir: In-Memory Execution and Advanced Encryption Techniques
The Ymir ransomware variant is unusual for its in-memory operation. Utilizing memory functions like malloc, memmove, and memcmp, it evades detection by residing entirely in the system memory. On launch, Ymir performs system reconnaissance, including retrieving system time and date, process details, and uptime to detect sandboxed environments and avoid rendering the system inoperable.
Ymir encrypts files using the ChaCha20 cipher, a highly secure, efficient encryption algorithm. Files are appended with a random extension (e.g., “.6C5oy2dVr6”), and the ransom note, INCIDENT_REPORT.pdf, is generated in each directory with encrypted files. Kaspersky researchers have also noted Lingala language references in the ransomware’s code.
Ymir ransom note
Source: BleepingComputer
Ymir Delivers Ransom Demands with Unique Strategies
Following file encryption, Ymir alters the Windows Registry “legalnoticecaption” to display an extortion notice before a user logs in. Each ransom note claims that data theft has occurred, and Kaspersky suspects this was achieved through tools deployed before Ymir’s infection. For stealth, Ymir uses PowerShell to erase its executable, avoiding forensic analysis and raising its chances of evading detection.
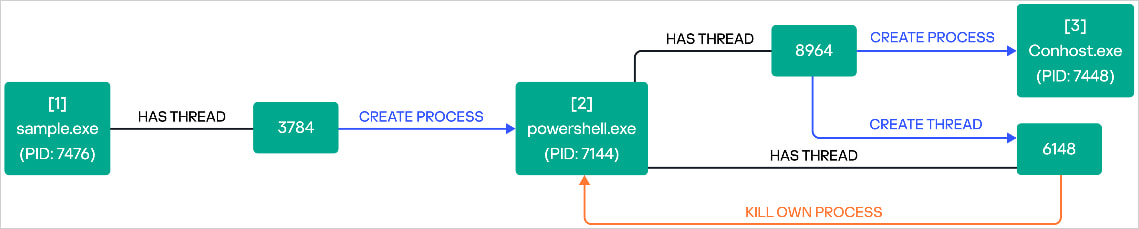 Ymir’s execution process
Ymir’s execution process
Source: Kaspersky