A new Android banking malware named DroidBot has surfaced, targeting credentials from over 77 cryptocurrency exchanges and banking apps across the UK, Italy, France, Spain, and Portugal.
Key Details
- Discovered by Cleafy researchers, DroidBot has been active since June 2024 and operates as a malware-as-a-service (MaaS) platform.
- Priced at $3,000 per month, DroidBot is being utilized by at least 17 affiliate groups, each customizing their payloads for specific regional and application targets.
- Despite lacking sophisticated features, DroidBot has already caused 776 unique infections across Europe and Turkey. Researchers believe the malware is still under heavy development, with plans to expand into Latin America.
DroidBot MaaS Operation
DroidBot’s creators, believed to be Turkish, provide affiliates with:
- Malware builders to create custom payloads.
- Command and Control (C2) infrastructure for managing attacks.
- A central administration panel for issuing commands and retrieving stolen data.
- Access to documentation, support, and updates via Telegram.
Creators claiming DroidBot works well on Android 14
Source: Cleafy
Features for Affiliates
- Target customization (e.g., regional apps, language preferences).
- Detailed control through an admin panel.
- Support for inexperienced attackers, lowering the barrier for entry into cybercrime.
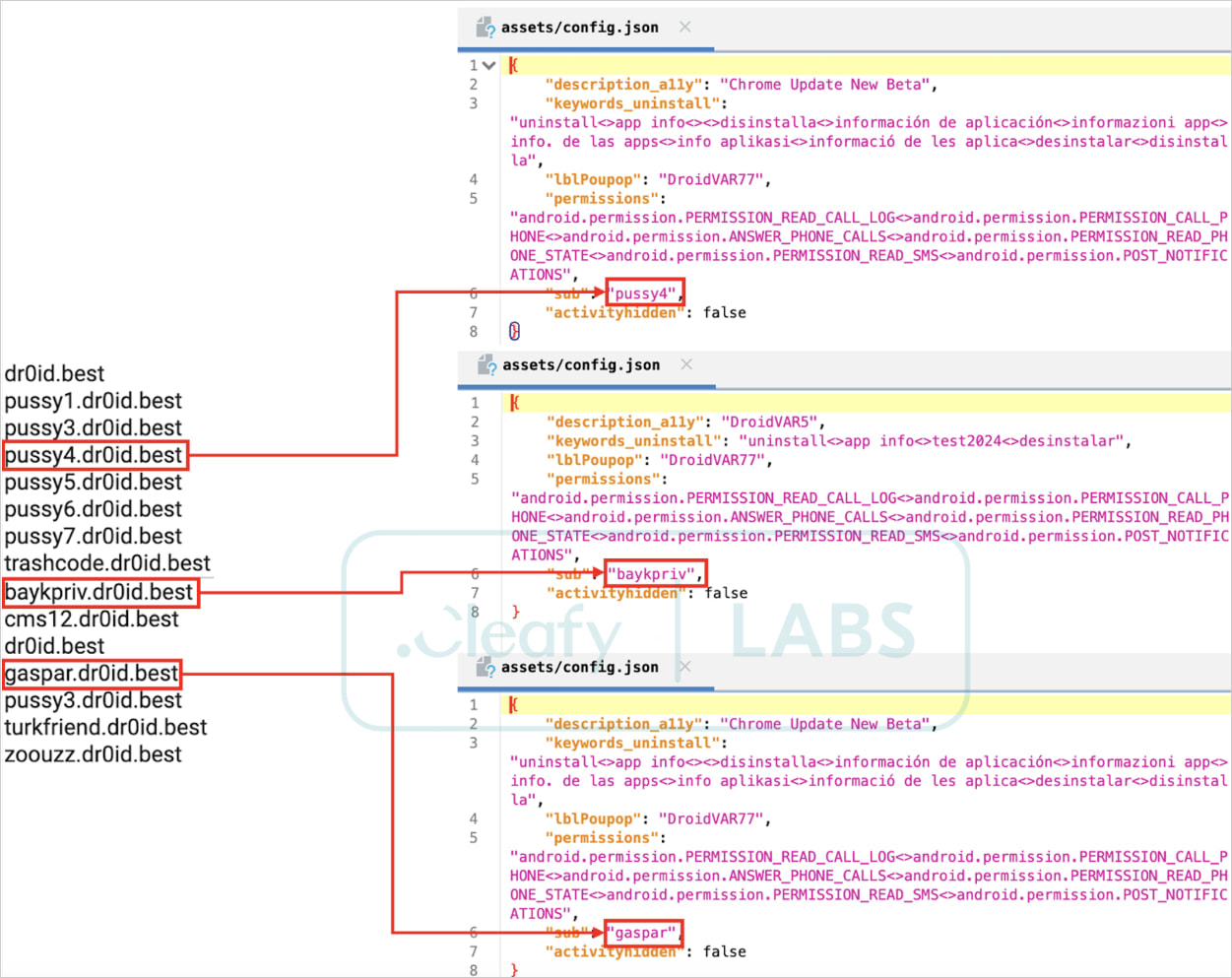 Affiliates extracted from the sample’s configuration
Affiliates extracted from the sample’s configuration
Source: Cleafy