Near-Field Communication (NFC) relay malware has grown massively popular in Eastern Europe, with researchers discovering over 760 malicious Android apps using the technique to steal people’s payment card information in the past few months.
Contrary to the traditional banking trojans that use overlays to steal banking credentials or remote access tools to perform fraudulent transactions, NFC malware abuses Android’s Host Card Emulation (HCE) to emulate or steal contactless credit card and payment data.
They capture EMV fields, respond to APDU commands from a POS terminal with attacker-controlled replies, or forward terminal requests to a remote server, which crafts the proper APDU responses to enable payments at the terminal without the physical cardholder present.
The technique was spotted in the wild for the first time in 2023 in Poland, followed by campaigns in the Czech Republic, and later, more massive attack waves in Russia.
Over time, multiple variants emerged following different practical approaches, including:
- Data harvesters that exfiltrate EMV fields to Telegram or other endpoints,
- Relay toolkits that forward APDUs to remote paired devices,
- “Ghost-tap” payments where HCE responses are manipulated to authorize POS transactions in real time,
- and PWAs or fake bank apps that are registered as the default payment handler on Android.
According to mobile security firm Zimperium, a member of Google’s ‘App Defense Alliance,’ the popularity of NFC malware on Android has exploded lately, particularly in Eastern Europe.
“What began as just a few isolated samples has now expanded to more than 760 malicious apps observed in the wild—demonstrating that NFC relay abuse is not slowing down but continuing to accelerate,” explains Zimperium.
“Campaigns previously documented by other vendors are now broadening their reach to additional regions, including Russia, Poland, the Czech Republic, Slovakia, and others.”
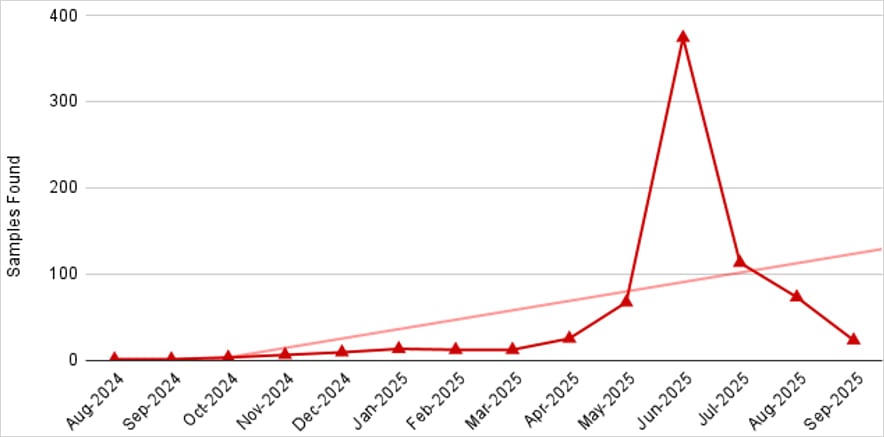
Source: Zimperium
The firm has identified over 70 command-and-control (C2) servers and app distribution hubs supporting these campaigns, as well as dozens of Telegram bots and private channels used to exfiltrate stolen data or coordinate operations.
The apps used to distribute the malware impersonate Google Pay or financial institutions such as Santander Bank, VTB Bank, Tinkoff Bank, ING Bank, Bradesco Bank, Promsvyazbank (PSB), and several others.
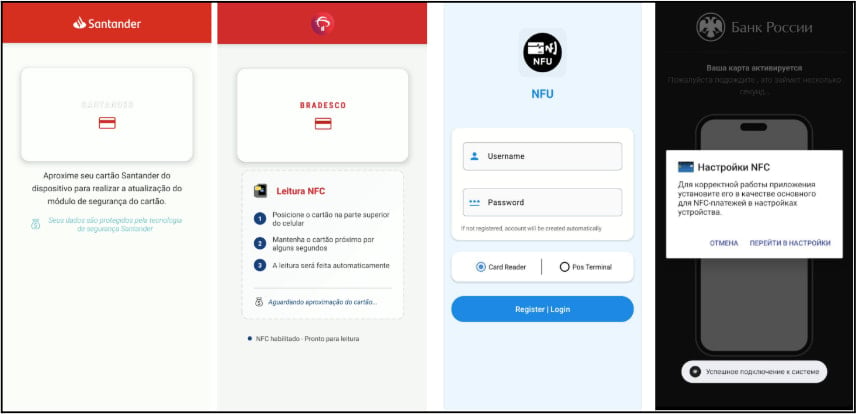
Source: Zimperium
Android users are advised to never install APKs from outside Google Play unless they explicitly trust the publisher, only install banking apps from the official bank links, and check for suspicious permissions, such as NFC access or foreground service privileges.
Additionally, it is recommended to regularly scan your device with Play Protect, Android’s built-in anti-malware tool, and to disable NFC if not needed.
The complete list of the APKs Zimperium discovered in the wild is available here.
