A phishing campaign is targeting Microsoft Active Directory Federation Services (ADFS) using spoofed login pages to steal credentials and bypass multi-factor authentication (MFA) protections.
Targeted Organizations
- Discovered by Abnormal Security, the campaign primarily targets:
- Education
- Healthcare
- Government organizations
- At least 150 organizations have been affected.
Attack Goals
- Compromise corporate email accounts to send phishing emails within the organization.
- Conduct financially motivated attacks such as business email compromise (BEC) to divert payments to threat actors.
How the Attack Works
1. Spoofing ADFS Login Pages
- ADFS is an authentication system that enables Single Sign-On (SSO) for internal and cloud-based applications.
- Attackers send phishing emails impersonating the IT team, asking users to update security settings.
Sample of a phishing email used in the attacks
Source: Abnormal Security
- Clicking the link redirects victims to a fake ADFS login page, which looks identical to the real one.
2. Capturing Credentials and MFA Codes
- The phishing site asks for username, password, and MFA code or tricks victims into approving a push notification.
- Templates target common MFA methods:
- Microsoft Authenticator
- Duo Security
- SMS Verification
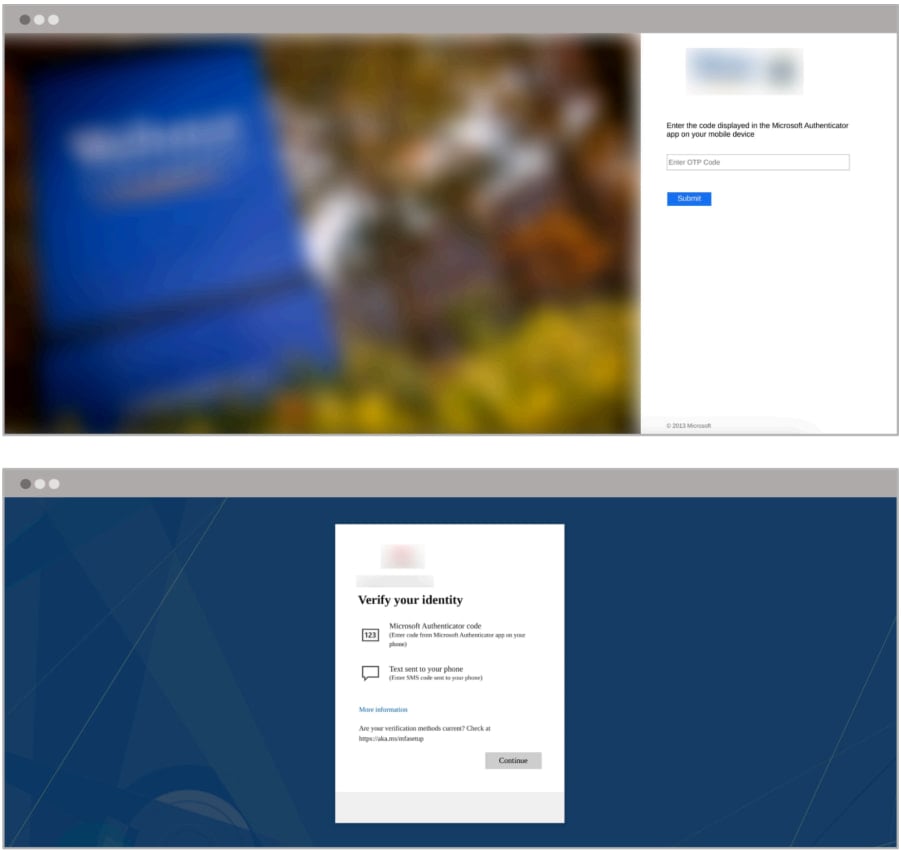 Two of the many available MFA bypass screens
Two of the many available MFA bypass screens
Source: Abnormal Security