A phishing campaign targeting automotive, chemical, and industrial manufacturing companies in Germany and the UK has been leveraging HubSpot’s Free Form Builder and DocuSign-like PDFs to steal Microsoft Azure account credentials.
Overview of the attack
Source: Unit 42
Key Findings:
- Scope of Attack: The campaign, active from June to September 2024, reportedly compromised approximately 20,000 accounts across European companies, according to Palo Alto Networks’ Unit 42 researchers.
- Abuse of HubSpot: Threat actors used HubSpot Form Builder to craft at least 17 deceptive forms, redirecting victims to credential-harvesting pages mimicking Microsoft Outlook Web App, Azure login portals, and other legitimate services.
- Delivery Mechanism: Phishing emails branded with DocuSign contained links to HubSpot forms via PDFs or embedded HTML. These emails bypassed some detection mechanisms due to the use of a legitimate service (HubSpot).
Attack Workflow:
- Phishing Email: Emails mimicked DocuSign or other trusted services with links pointing to HubSpot forms.
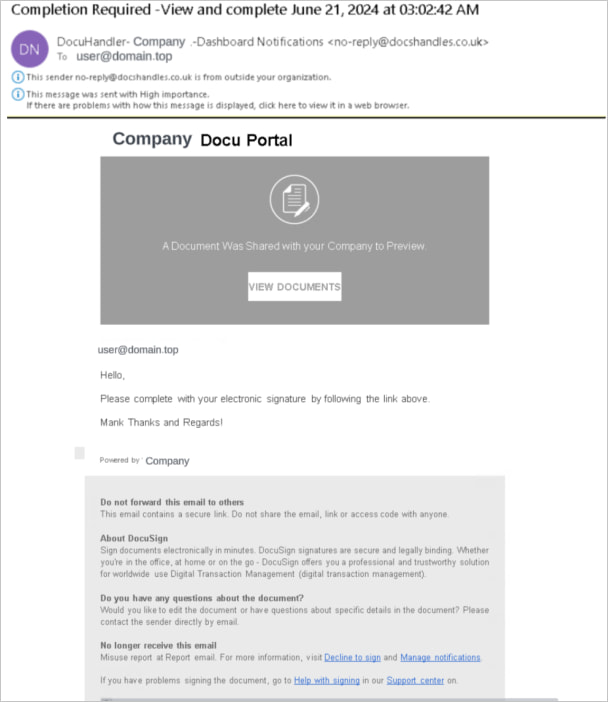
Phishing email sample
Source: Unit 42 - HubSpot Forms: Victims interacted with fake forms hosted on HubSpot’s legitimate platform.
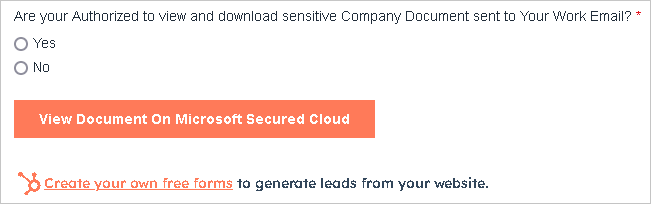
Deceptive HubSpot form
Source: Unit 42 - Credential Harvesting: Victims were redirected to attacker-controlled sites hosted on “.buzz” domains impersonating login portals.
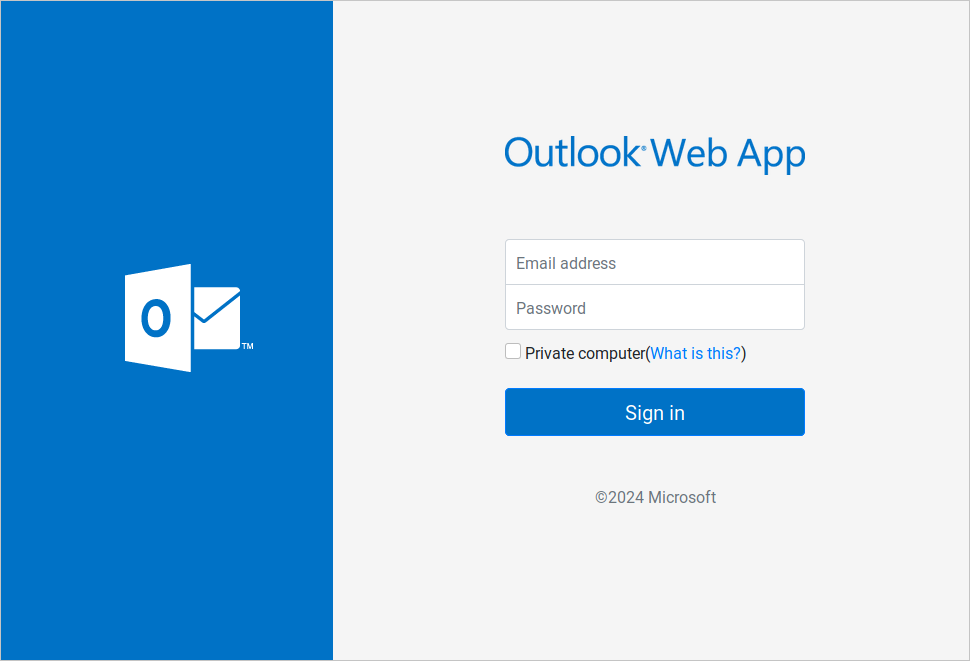
Phishing page targeting Outlook accounts
Source: Unit 42 - Post-Compromise Activity:
- Threat actors used VPNs to simulate the victim’s country.
- If IT attempted to recover the compromised account, attackers engaged in a “tug-of-war” by initiating password resets.