A newly emerged hacking group, known as the “Belsen Group,” has leaked the configuration files, IP addresses, and VPN credentials for more than 15,000 FortiGate devices. The data, containing sensitive technical details, was made freely available on the dark web, posing significant risks to organizations worldwide.
Post on hacking forum
Source: BleepingComputer
Details of the Leak
The leak, announced on cybercrime forums and through a Tor-hosted website, appears to be an attempt to promote the Belsen Group. The group claimed the data spans both governmental and private sectors across numerous countries.
The 1.6 GB archive, organized by country and further subfolders per IP address, includes:
- Configuration files (
configuration.conf), which detail firewall rules and private keys. - VPN credentials (
vpn-passwords.txt), some of which are in plain text.
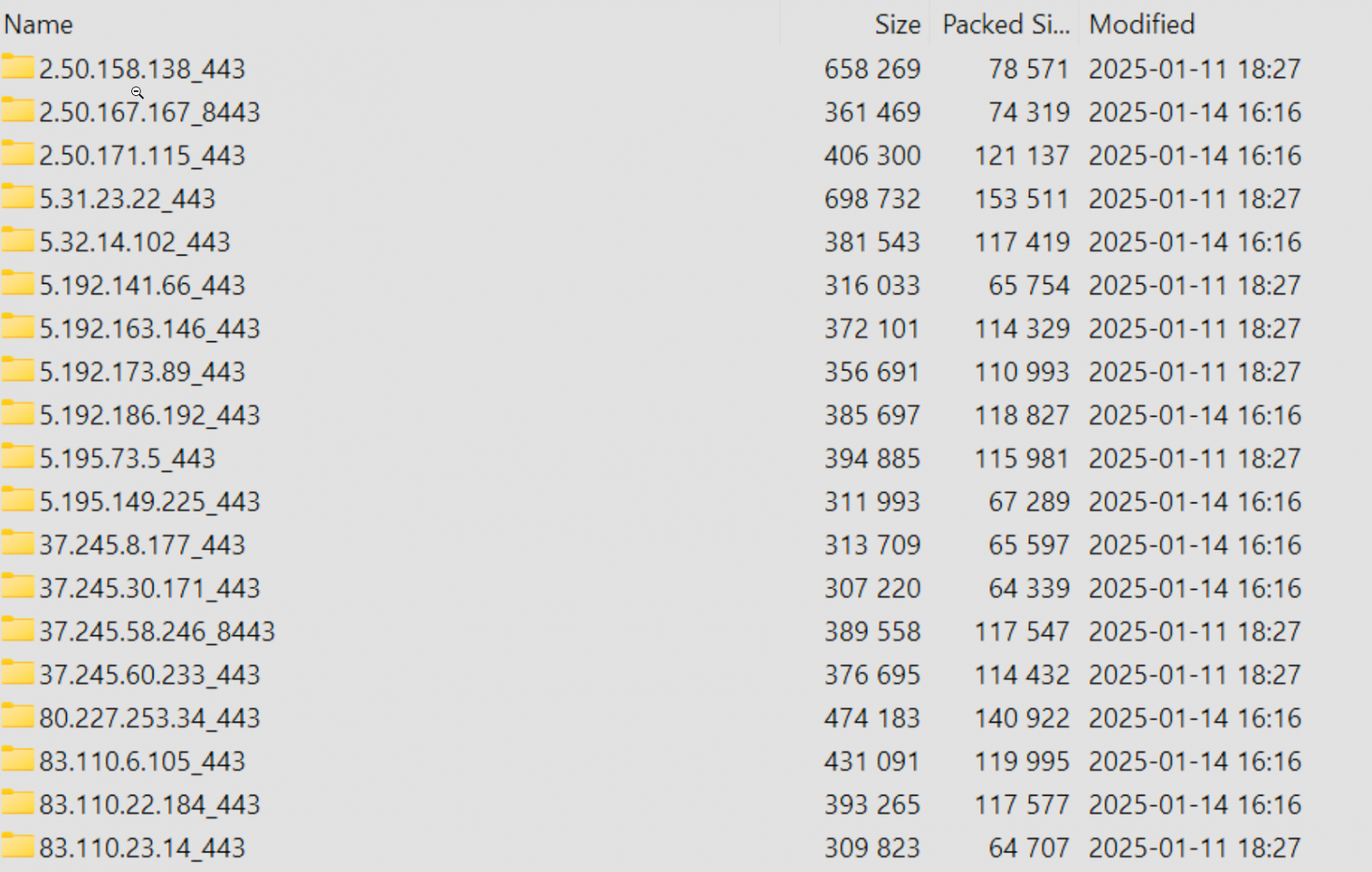 IP address folder for FortiGate devices and their configs
IP address folder for FortiGate devices and their configs
Source: Beaumont
Connection to CVE-2022–40684
Cybersecurity expert Kevin Beaumont linked the leak to CVE-2022–40684, a critical zero-day vulnerability disclosed in 2022. This flaw allowed attackers to download FortiGate configuration files and create rogue admin accounts, such as ‘fortigate-tech-support.’
Beaumont noted that the leaked data appears to have been collected in October 2022 during the height of exploitation activity for this vulnerability. Interestingly, while most of the impacted devices were running FortiOS versions 7.0.0–7.0.6 or 7.2.0–7.2.2, which were vulnerable, the latter version was patched against CVE-2022–40684 on October 3, 2022, raising questions about the exploit method for devices using that firmware.