Ficora Botnet
Ficora is a modernized variant of the Mirai botnet, designed specifically to exploit flaws in D-Link routers. According to Fortinet telemetry, Ficora shows random targeting but has had notable surges in activity in October and November 2024, particularly in Japan and the United States.
Location of devices infected by Ficora
Source: Fortinet
Key Characteristics:
- Payload Delivery: Deploys a shell script named
multito download and execute malware via multiple methods (wget,curl,ftpget, andtftp). - Brute Force Functionality: Employs hard-coded credentials to infect other Linux-based devices.
- DDoS Capabilities: Implements UDP flooding, TCP flooding, and DNS amplification, maximizing the impact of its attacks.
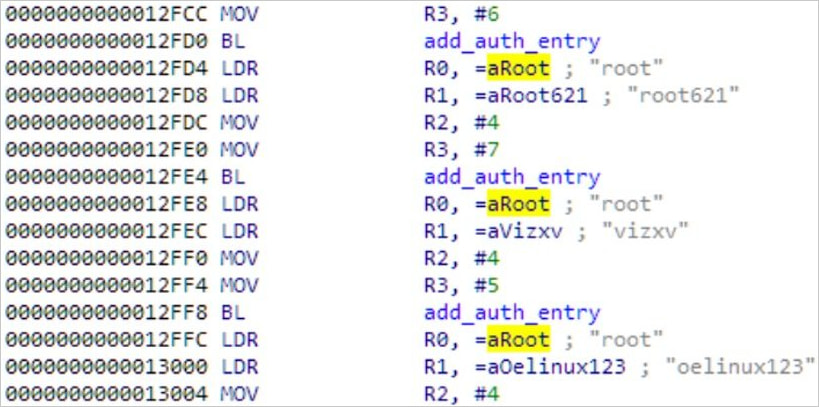 Ficora’s brute-forcing function
Ficora’s brute-forcing function
Source: Fortinet
Capsaicin Botnet
Capsaicin, a variant of the Kaiten botnet, is believed to originate from the Keksec group, known for malware like EnemyBot. While its activity spiked briefly between October 21-22, it primarily targeted East Asian devices.
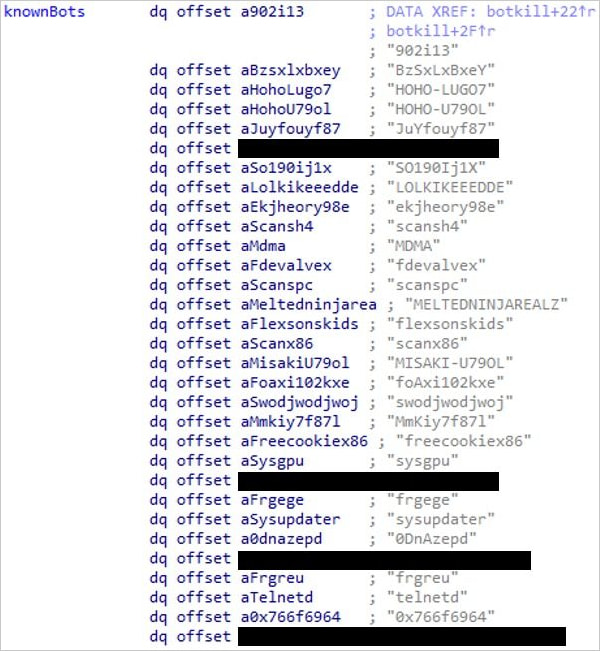 Names of other botnet malware Capsaicin disables
Names of other botnet malware Capsaicin disables
Source: Fortinet
Key Characteristics:
- Infection Mechanism: Uses a downloader script (
bins.sh) to fetch binaries prefixed with ‘yakuza’ for multiple architectures (e.g., arm, mips, sparc, x86). - Botnet Neutralization: Actively disables other botnet payloads present on infected devices.
- DDoS Capabilities: Similar to Ficora, Capsaicin supports UDP and TCP floods while also gathering host information for exfiltration to its command-and-control (C2) server.
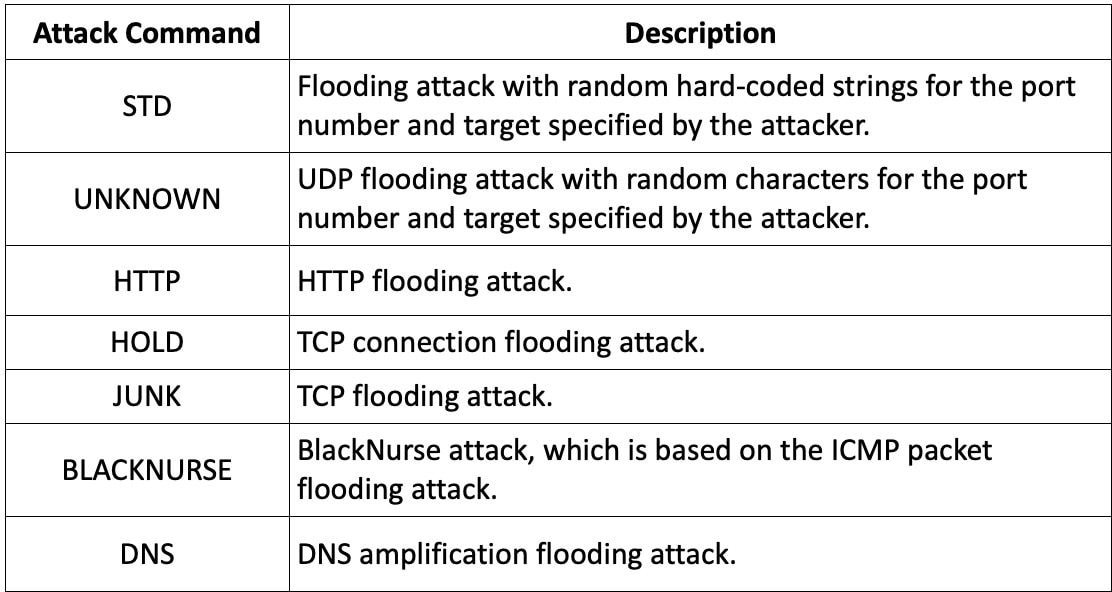 Capsaicin DDoS commands
Capsaicin DDoS commands
Source: Fortinet