In the world of cybersecurity, analysts at Proofpoint have uncovered three distinct attack chains that all ultimately lead to malware infections. These attacks deliver a range of malicious payloads, including DarkGate, Matanbuchus, NetSupport, Amadey Loader, XMRig, a clipboard hijacker, and Lumma Stealer.
The first attack chain, associated with ClearFake, begins with users encountering a fake Google Chrome warning on compromised websites, alerting them to a webpage display issue. The warning directs users to copy a PowerShell script to install a “root certificate” and run it with administrative privileges.
PowerShell “Fix” Leads to Malware Infections
Proofpoint analysts identified three distinct attack chains, each varying slightly in their initial stages. However, the subsequent stages consistently lead to malware infections. The payloads delivered through these attacks include DarkGate, Matanbuchus, NetSupport, Amadey Loader, XMRig, a clipboard hijacker, and Lumma Stealer.
In the first attack chain, linked to ClearFake, users visiting compromised websites encounter a fake Google Chrome warning about a webpage display issue. The warning instructs users to copy a PowerShell script to install a “root certificate” and run it with administrative privileges.
Fake Google Chrome error
Source: Proofpoint
Executing this script triggers a series of actions:
- Flushing the DNS cache.
- Removing clipboard content.
- Displaying a decoy message.
- Downloading and executing additional payloads after performing anti-VM checks.
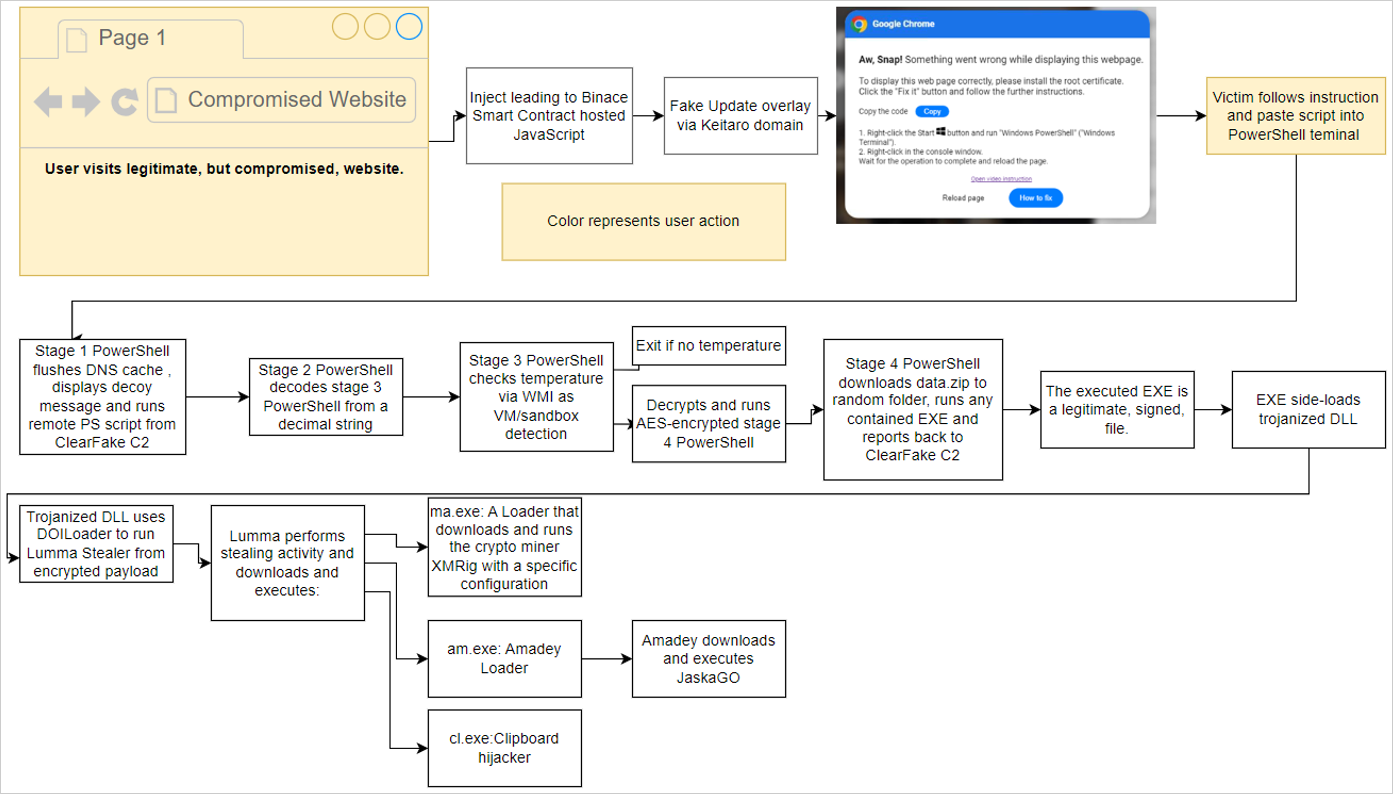 The ‘ClearFake’ attack chain
The ‘ClearFake’ attack chain
Source: Proofpoint
Upon executing this script, a series of actions are triggered that include flushing the DNS cache, removing clipboard content, displaying a decoy message, and downloading and executing additional payloads after conducting anti-VM checks.
The second attack chain, linked to the ClickFix campaign, involves injecting an iframe into compromised websites to display another fake Google Chrome error. Users are prompted to run a PowerShell script, resulting in the same malware infections as the first chain.
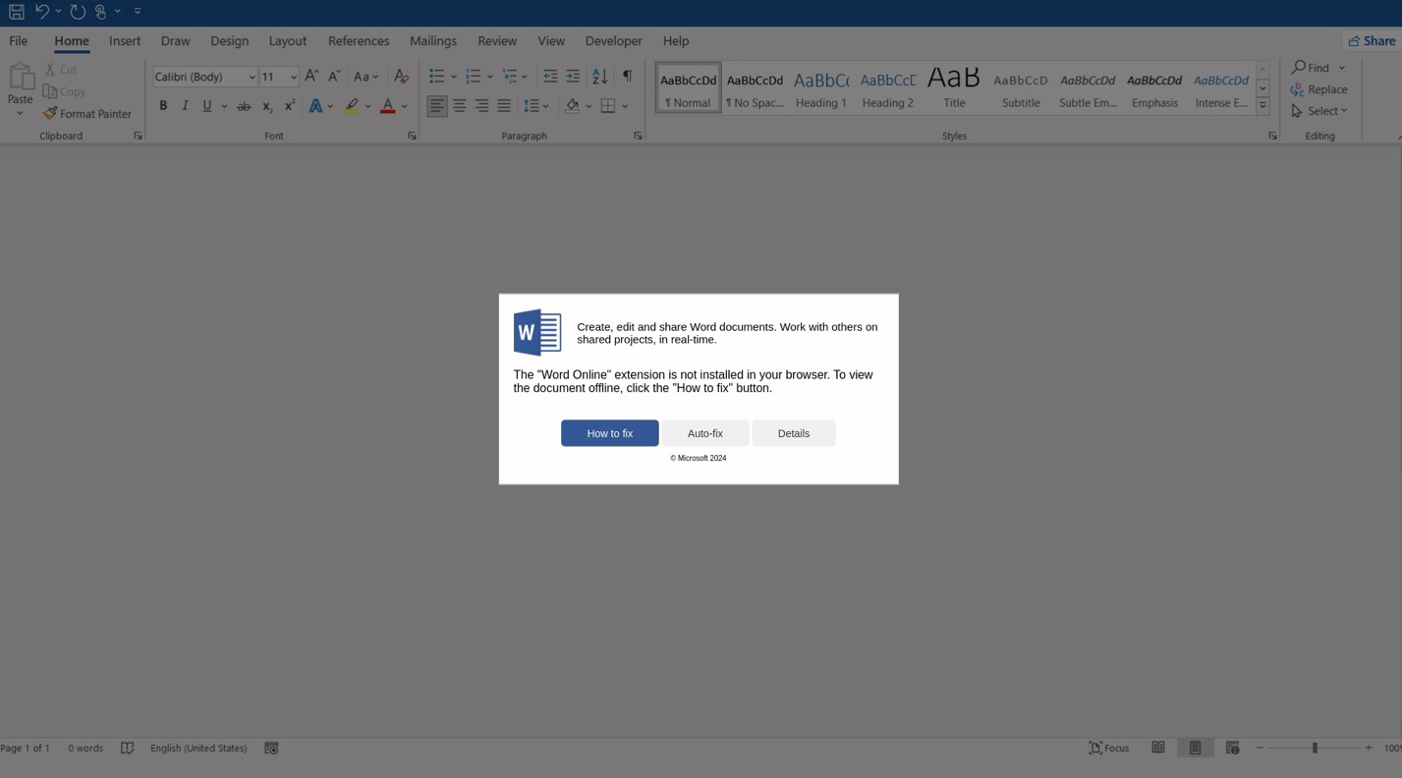 Fake Microsoft Word error leads to malware
Fake Microsoft Word error leads to malware
Source: Proofpoint
The third attack chain employs email-based tactics, with HTML attachments masquerading as Microsoft Word documents prompting users to install the “Word Online” extension. The error message offers “How to fix” and “Auto-fix” options, both of which lead to the execution of malicious PowerShell commands or the download of harmful files.
In today’s cybernews, it is crucial for users to be vigilant and cautious when encountering unexpected warnings or prompts, as they could be part of a larger malware infection scheme. Stay informed and stay safe in the ever-evolving landscape of cybersecurity threats.