CRON#TRAP is a recent phishing attack discovered by Securonix researchers, targeting corporate networks through a Linux VM deployed via phishing emails. The email, disguised as a survey from OneAmerica, contains a 285MB ZIP file with a Windows shortcut and a custom QEMU virtual machine. When the file is opened, it installs the Linux VM, named PivotBox, with a pre-configured backdoor for remote access.
How CRON#TRAP Operates
- Infection via Phishing: A phishing email with a ZIP attachment claims to be a survey but hides a malicious payload.
- VM Deployment: Executing the file installs a TinyCore Linux VM on the host through QEMU, which appears legitimate and is digitally signed, bypassing some security scrutiny.
Start.bat batch file installing the QEMU Linux virtual machine
Source: BleepingComputer
3. Chisel Backdoor: The VM contains Chisel, a tunneling tool that uses HTTP and SSH to communicate with a remote Command and Control (C2) server.
4. Persistence and Commands: The backdoor enables persistence via bootlocal.sh, ensuring the VM restarts on reboot. Commands include get-host-shell (to access an interactive shell) and get-host-user (to assess user privileges), with actions ranging from network surveillance to data exfiltration.
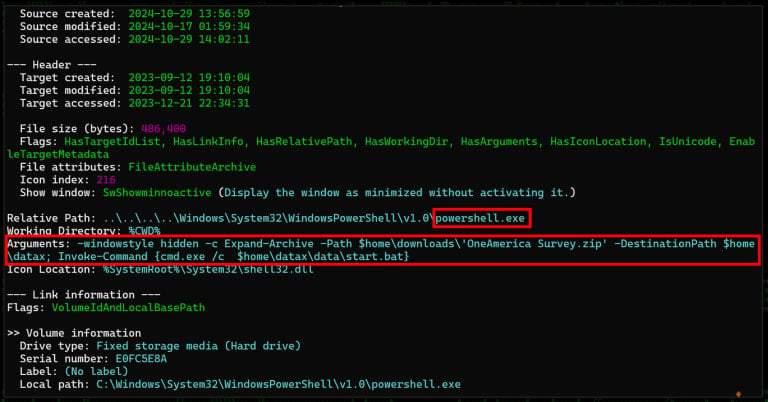 LNK file contents
LNK file contents
Source: Securonix