A new critical severity vulnerability found in American Megatrends International’s MegaRAC Baseboard Management Controller (BMC) software can let attackers hijack and potentially brick vulnerable servers.
MegaRAC BMC provides “lights-out” and “out-of-band” remote system management capabilities that help admins troubleshoot servers as if they were physically in front of the devices. The firmware is used by over a dozen server vendors that provide equipment to many cloud service and data center providers, including HPE, Asus, ASRock, and others.
Remote unauthenticated attackers can exploit this maximum severity security flaw (tracked as CVE-2024-54085) in low-complexity attacks that don’t require user interaction.
“A local or remote attacker can exploit the vulnerability by accessing the remote management interfaces (Redfish) or the internal host to the BMC interface (Redfish),” Eclypsium explained in a Tuesday report.
“Exploitation of this vulnerability allows an attacker to remotely control the compromised server, remotely deploy malware, ransomware, firmware tampering, bricking motherboard components (BMC or potentially BIOS/UEFI), potential server physical damage (over-voltage / bricking), and indefinite reboot loops that a victim cannot stop.”
Eclypsium security researchers discovered the CVE-2024-54085 auth bypass while analyzing patches issued by AMI for CVE-2023-34329, another authentication bypass the cybersecurity company disclosed in July 2023.
While Eclypsium confirmed that HPE Cray XD670, Asus RS720A-E11-RS24U, and ASRockRack are vulnerable to CVE-2024-54085 attacks if left unpatched, it also added that “there are likely to be more affected devices and/or vendors.”
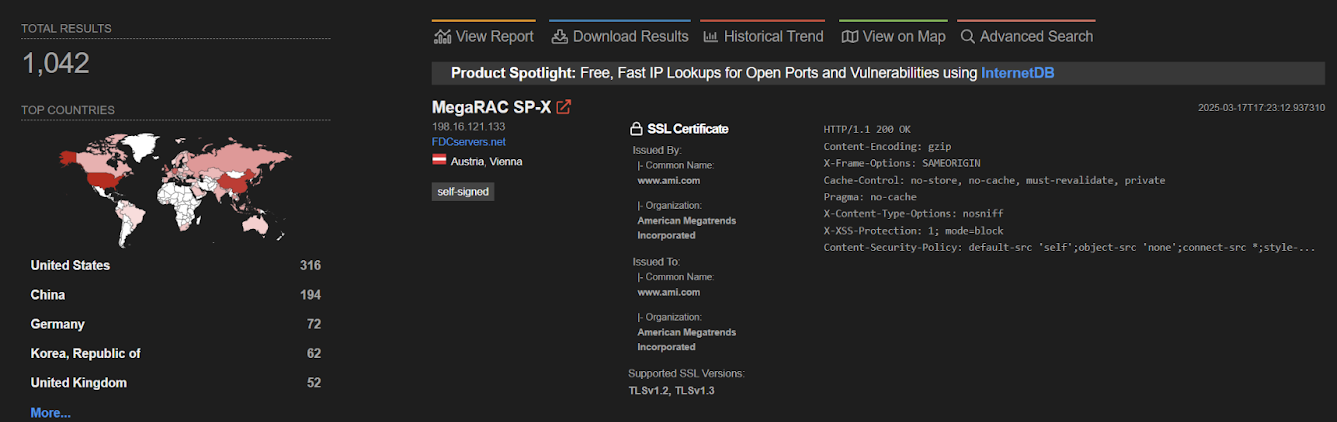
Using Shodan, the security researchers found over 1,000 servers online that are potentially exposed to Internet attacks.
As part of their research into MegaRAC vulnerabilities (collectively tracked as BMC&C), Eclypsium analysts disclosed five more flaws in December 2022 and January 2023 (CVE-2022-40259, CVE-2022-40242, CVE-2022-2827, CVE-2022-26872, and CVE-2022-40258) that can be exploited to hijack, brick, or remotely infect compromised servers with malware.
In July 2023, they also found a code injection vulnerability (CVE-2023-34330) that can used in attacks to inject malicious code via the Redfish remote management interfaces exposed to remote access and which can be chained with the previously discovered bugs.
Specifically, CVE-2022-40258, which involves weak password hashes for Redfish & API, can help attackers crack the administrator passwords for the BMC chip’s admin accounts, making the attack even more straightforward.
While Eclypsium said the CVE-2024-54085 auth bypass flaw hasn’t been used in attacks, and no exploits have been found in the wild, it also added that creating an exploit is “not challenging” given that the firmware binaries are not encrypted.
Network defenders are advised to apply patches released one week ago, on March 11, by AMI, Lenovo, and HPE as soon as possible, not to expose AMI MegaRAC instances online, and to monitor server logs for suspicious activity.
“To our knowledge, the vulnerability only affects AMI’s BMC software stack. However, since AMI is at the top of the BIOS supply chain, the downstream impact affects over a dozen manufacturers,” Eclypsium added today.
“AMI has released patches to its OEM computing manufacturers’ customers. Those vendors must incorporate the fixes into updates and publish notifications to their customers. Note that patching these vulnerabilities is a non-trivial exercise, requiring device downtime.”
