APT36 Launches Cross-Platform ClickFix Attacks, Now Targeting Linux Users
The threat group known as APT36 (aka Transparent Tribe) has launched a new ClickFix campaign targeting all major desktop operating systems—Windows, Linux, and macOS—with tailored social engineering techniques to deliver malware.
What is ClickFix?
ClickFix is a social engineering technique that tricks users into manually executing malicious commands via Run dialogs or terminal windows. These attacks often masquerade as application errors, CAPTCHAs, or verification prompts, leading unsuspecting users to run malware payloads themselves.
ClickFix attacks have previously been observed targeting Windows users, often prompting them to run PowerShell or MSHTA commands that lead to info-stealers or ransomware infections. In 2024, similar tactics expanded to macOS, using fake Google Meet errors to deliver malware.
New Linux-Focused Attack Flow
In a new campaign observed by Hunt.io, APT36 is now leveraging ClickFix against Linux users. The threat actors are using a malicious website impersonating India’s Ministry of Defence, with a fake press release used as bait.
Malicious website mimicking India’s Ministry of Defence
Source: Hunt.io
Once a visitor lands on the site, their operating system is fingerprinted to serve a tailored attack path:
-
Windows users are redirected to a full-screen warning about content restrictions. Clicking “Continue” copies a malicious MSHTA command to the clipboard, which the user is instructed to paste into a terminal window. This command runs a .NET loader, displaying a decoy PDF while silently connecting to a command-and-control (C2) server.
-
Linux users see a CAPTCHA page that copies a shell command to their clipboard after clicking the “I’m not a robot” button. The victim is then instructed to open the Run dialog (ALT+F2), paste the command, and execute it.
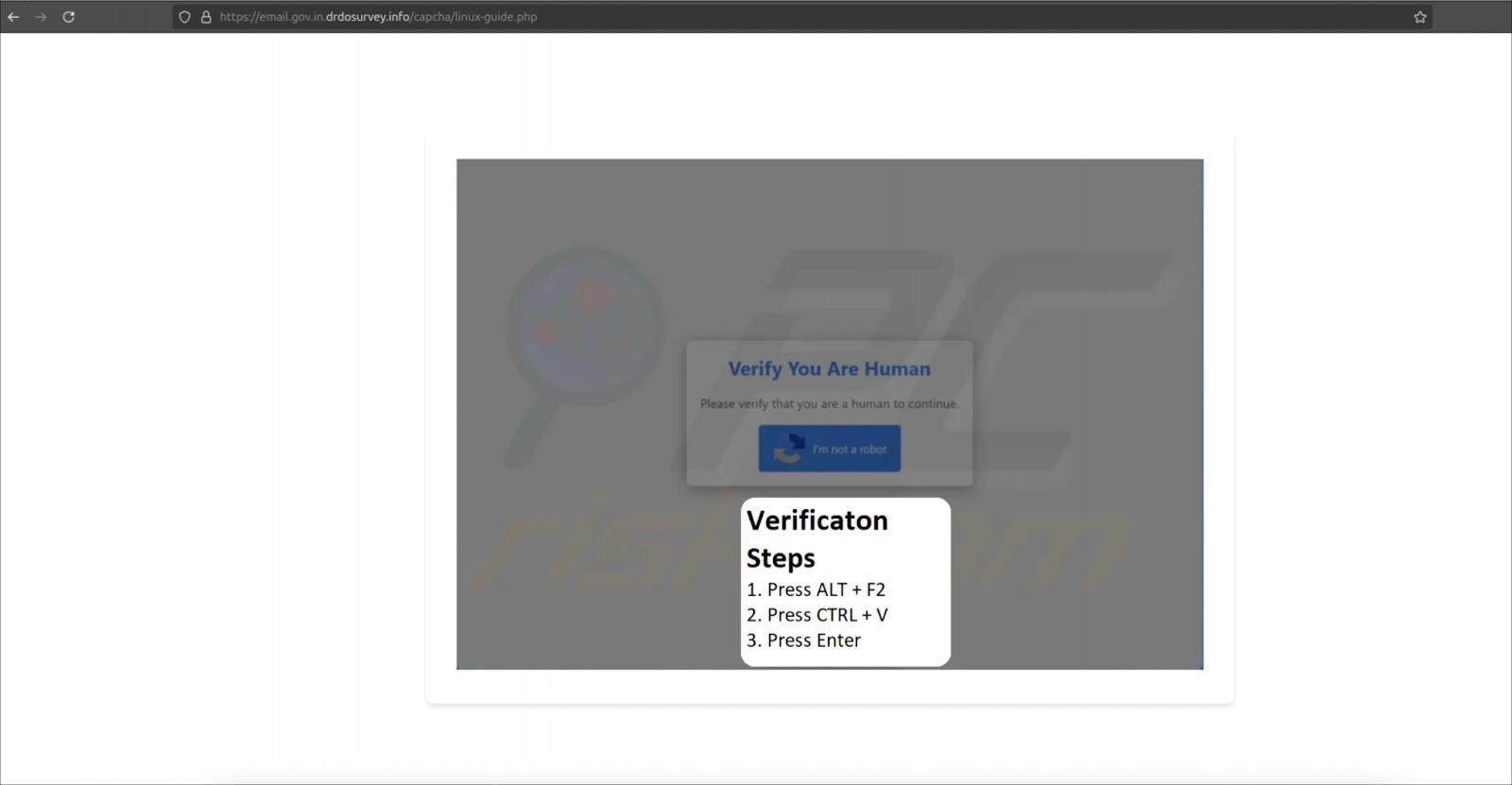 Instructions for Linux users
Instructions for Linux users
Source: Hunt.io