Microsoft is warning that an ongoing phishing campaign impersonating Booking.com is using ClickFix social engineering attacks to infect hospitality workers with various malware, including infostealers and RATs.
The campaign started in December 2024 and continues today, targeting employees at hospitality organizations such as hotels, travel agencies, and other businesses that use Booking.com for reservations.
The threat actors’ goal is to hijack employee accounts on the Booking.com platform and then steal customer payment details and personal information, potentially using it to launch further attacks on guests.
Microsoft security researchers who discovered this campaign attribute the activity to a threat group it tracks as ‘Storm-1865.’
ClickFix meets Booking.com
ClickFix is a relatively new social engineering attack that displays fake errors on websites or in phishing documents and then prompts users to perform a “fix” “captcha” to view the content.
However, these fake fixes are actually malicious PowerShell or other malicious commands that download and install infostealing malware and remote access trojans on Windows and Mac devices.
This type of attack has become increasingly popular and is used by a wide variety of threat actors, including ransomware gangs and North Korean hackers.
In the phishing campaign discovered by Microsoft, the threat actors send emails impersonating pretending to be guests inquiring about a negative Booking.com review, requests from prospective clients, account verification alerts, and others.
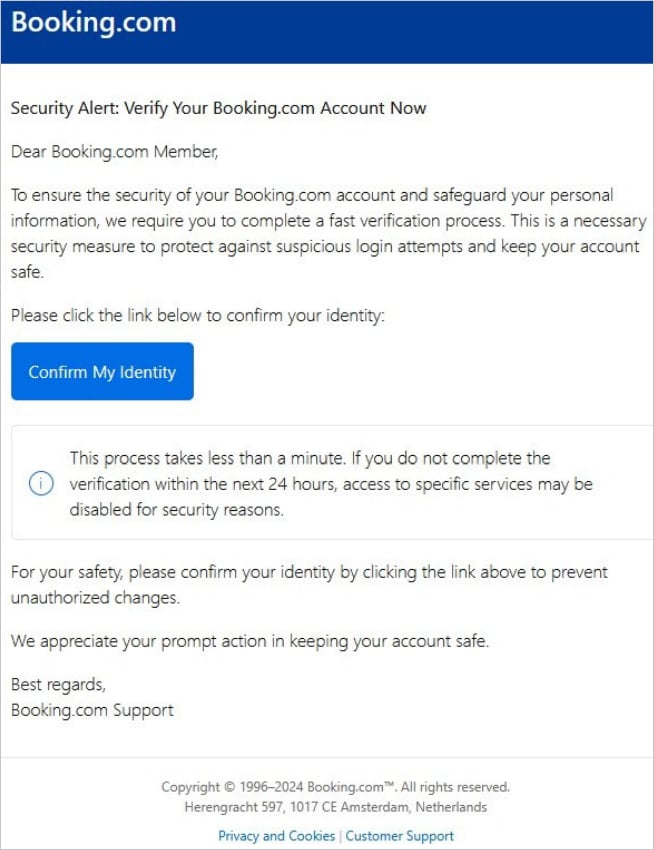
Source: Microsoft
These emails contain either a PDF attachment containing a link or an embedded button, both taking the victim to a fake CAPTCHA page.
A fake CAPTCHA in ClickFix campaigns has become popular as it adds a false sense of legitimacy to the process, hoping to trick recipients into lowering their guard.
When solving the malicious CAPTCHA, a hidden mshta.exe command will be copied to the Windows clipboard to perform the “human verification” process. The target is told to perform this verification by opening the Windows Run command, pasting the clipboard’s contents into the Run field, and executing it.
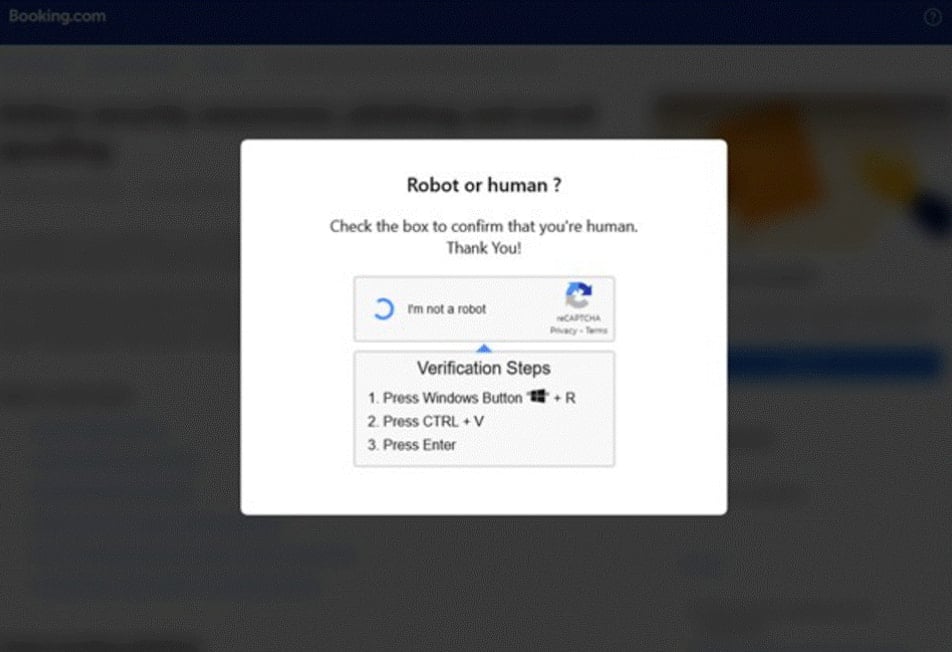
Source: Microsoft
The victims only see keyboard shortcuts, not the content copied to the clipboard, so they have no indication they’re about to execute a command on their system. Hence, those with less experience with computers are likely to fall for the trap.
In this campaign, Microsoft says that the copied code is a mshta.exe that executes a malicious HTML file [VirusTotal] on the attacker’s server.

Source: Microsoft
Executing the command downloads and installs a wide variety of remote access trojans and infostealing malware, including XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT.
“Depending on the specific payload, the specific code launched through mshta.exe varies,” explains Microsoft’s report.
“Some samples have downloaded PowerShell, JavaScript, and portable executable (PE) content.”
“All these payloads include capabilities to steal financial data and credentials for fraudulent use, which is a hallmark of Storm-1865 activity.”
.jpg)
Source: Microsoft
To defend against these attacks, Microsoft recommends always confirming the legitimacy of the sender’s address, being extra careful when met with urgent calls to action, and looking for typos that could give away scammers.
It is also advisable to verify the Booking.com account status and pending alerts by logging in on the platform independently instead of following links from emails.
