A set of 57 Chrome extensions with 6,000,000 users have been discovered with very risky capabilities, such as monitoring browsing behavior, accessing cookies for domains, and potentially executing remote scripts.
These extensions are ‘hidden,’ meaning they don’t show up on Chrome Web Store searches, nor do search engines index them, and can only be installed if the user has the direct URL.
Typically, such extensions are private software like internal company tools or add-ons still under development. Still, threat actors might be using them to evade detection while aggressively pushing them through ads and malicious sites.
Risky Chrome extensions
The extensions were discovered by Secure Annex researcher John Tuckner, who uncovered the first 35 after examining what he claims is a suspicious extension named ‘Fire Shield Extension Protection.’
The extension is heavily obfuscated and contains callbacks to an API for sending information collected from the browser.
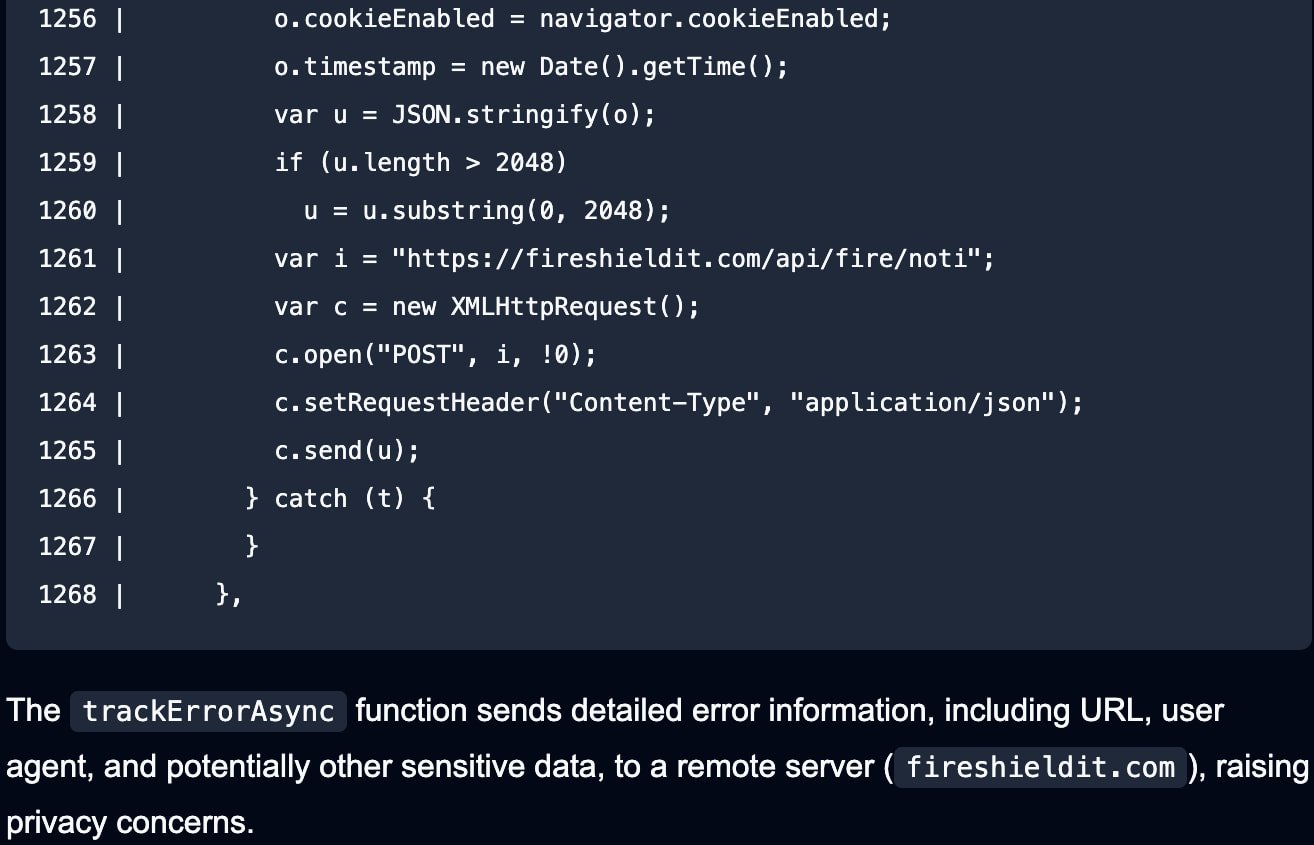
Source: Secure Annex
Through a domain called “unknow.com” contained in the extension, Tuckner found additional extensions containing the same domain that claim to provide ad-blocking or privacy protection services.
.jpg)
Source: Secure Annex
However, all of these include overly broad permissions allowing them to perform the following actions:
- Access cookies, including sensitive headers (e.g., ‘Authorization’)
- Monitor user browsing behavior
- Modify search providers (and results)
- Inject and execute remote scripts on visited pages via iframes
- Activate advanced tracking remotely
While Tuckner didn’t catch any extensions stealing user passwords or cookies, the excessively risky capabilities, heavily obfuscated code, and hidden logic were enough for the researcher to label them as risky and, potentially, spyware.
“There are additional obfuscated signals in other functions that there is significant command and control potential like the ability to list top sites visited, open/close tabs, get top sites visited, and run many of the capabilities above in an ad hoc manner,” explains Tuckner.
“Many of these capabilities have not been validated, but again, the presence of this capability in 35 extensions which claim to do simple things like protect you from malicious extensions is quite concerning.”
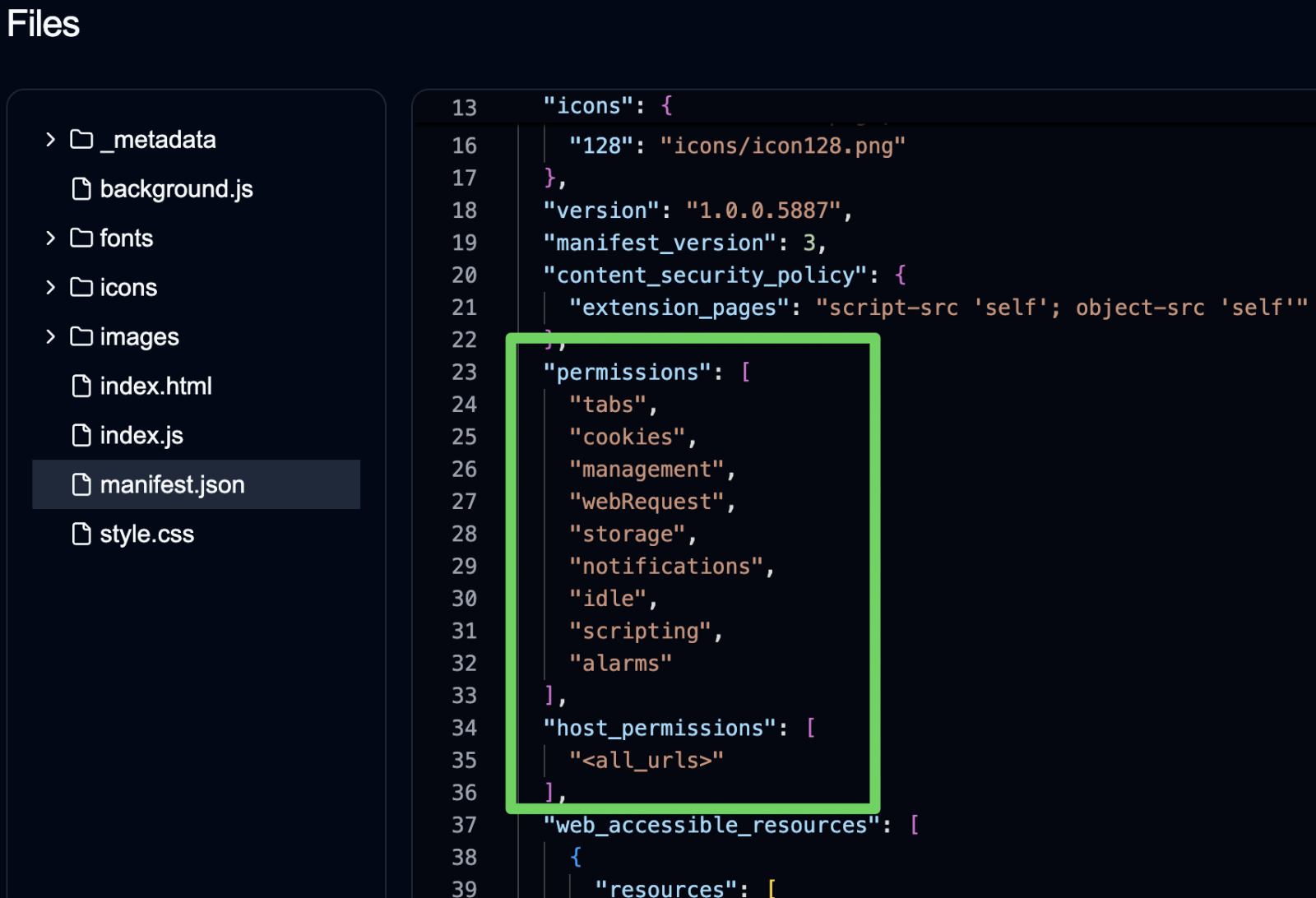
Source: Secure Annex
Earlier today, the researcher added 22 more extensions believed to belong to the same operation, taking the total to 57 extensions used by 6 million people. Some of the newly added extensions are public, too.
Tuckner says that many of the extensions have been removed from the Chrome Web Store following his report from last week, but others still remain.
Source: BleepingComputer
The complete list is available here, with the ones with the highest download counts listed below:
- Cuponomia – Coupon and Cashback (700,000 users, public)
- Fire Shield Extension Protection (300,000 users, unlisted)
- Total Safety for Chrome™ (300,000 users, unlisted)
- Protecto for Chrome™ (200,000 users, unlisted)
- Browser WatchDog for Chrome (200,000 users, public)
- Securify for Chrome™ (200,000 users, unlisted)
- Browser Checkup for Chrome by Doctor (200,000 users, public)
- Choose Your Chrome Tools (200,000 users, unlisted)
If you have any of the above installed, it is recommended that you remove them immediately and, out of an abundance of caution, perform password resets on online accounts.
Google told BleepingComputer that they are aware of Tuckner’s report and are investigating the extensions.
BleepingComputer also contacted the developer of these extensions with questions about the obfucated code but has not received a reply at this time.