Phishing remains one of cybersecurity’s most enduring threats, not because defenders aren’t evolving, but because attackers are adapting even faster.
Today’s most effective campaigns aren’t just built on spoofed emails or shady domains. They exploit something far more insidious: trust in the tools and services we use every day, leading to zero-hour phishing.
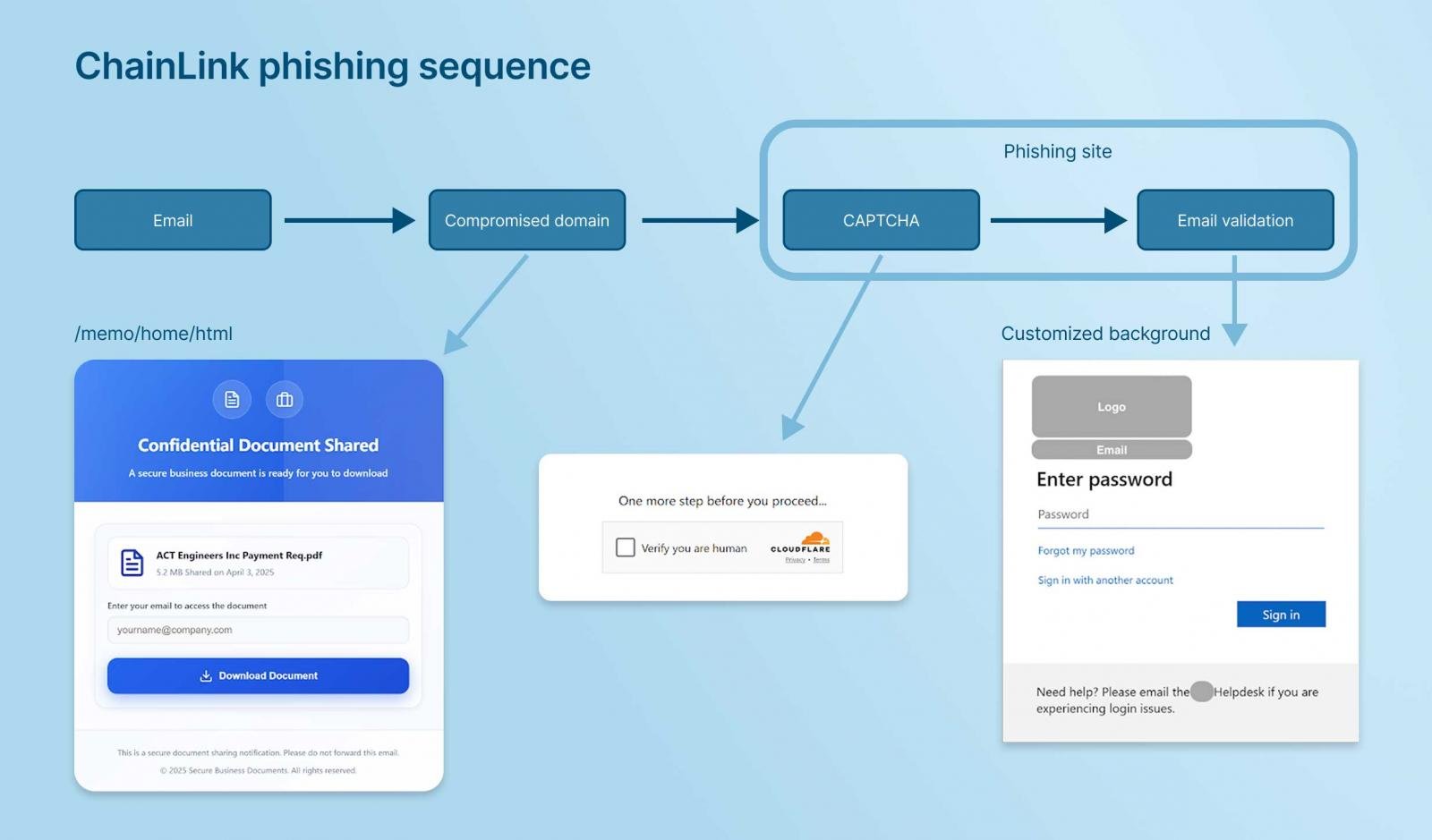
The Rise of ChainLink Phishing
Traditional phishing relied on easily identifiable red flags such as suspicious senders and questionable URLs. But modern phishing has matured.
Attackers now deploy chained sequences, funneling a victim from email through trusted infrastructure before harvesting credentials.
An employee might receive a link from what appears to be Google Drive or Dropbox. At first glance, there’s nothing unusual. But after the initial click, the user is quietly routed through a series of prompts, each looking credible on reputable sites, until they unknowingly hand over business-essential credentials to an attacker.
This technique, which we call ChainLink Phishing, relies on leveraging the legitimate platforms and reputable domains that enterprise tools allow and that IT security teams are oblivious to.
Keep Aware stops phishing attacks in real-time where they start: inside the browser.
By analyzing user behavior, form submissions, and site context, not just URLs, Keep Aware shuts down threats before credentials ever leave the page. Equip your security team with precise visibility, policy enforcement, and immediate threat response all from within the existing web browsers across the organization.
Why These Attacks Are So Effective
The browser has become the center of the knowledge worker’s universe. From code reviews to HR tasks, nearly every action begins and ends in a browser tab.
This centralization gives attackers a singular surface to exploit, yet it has been vastly underprotected.
Even the most security-aware employees can be deceived when a link appears to come from a known domain and follows the expected behavior. The user often believes they’re engaging in normal activity until it’s too late.
By using legitimate links, passing email authentication checks, and even inserting CAPTCHAs along the way, attackers sidestep traditional defenses and enable zero-hour phishing to succeed undetected.
CAPTCHAs and verification steps are now so common in everyday browsing that attackers exploit them as social engineering tactics, not only in phishing campaigns, but also in other browser-based threats like ClickFix.
“Known Good” Is No Longer Safe
This shift highlights a painful truth: “known good” is no longer a reliable security signal. In fact, it’s become the perfect disguise for bad actors.
To truly address threats like ChainLink Phishing, we need to move beyond static blocklists and domain-based filtering. The future of phishing protection lies in real-time analysis of web pages and users’ interactions with them.

When the Security Stack Can’t See the Threat
A phishing link that originates from a trusted service will often sail past email and network filters. Traffic to the phishing site is allowed unimpeded because the domain isn’t on an intel feed and its reputation is undamaged. And since no malware is deployed, just credential harvesting, endpoint tools have nothing to detect.
Despite having layered defenses like:
- Secure email gateways (SEGs)
- DNS filtering
- Secure web gateways (SWGs)
- EDR/AV
- Native browser protections
… Most organizations remain vulnerable. Why? Because these tools are designed to block known malicious web behavior and endpoint solutions are oblivious to credential-harvesting web forms. The subtle misuse of legitimate domains, combined with additional evasive techniques, leads to users falling victim to zero-hour phishing.
Defend Where Phishing Really Strikes
These sequenced attacks exploit trusted pathways, leading users to phishing sites that easily bypass traditional defenses. By the time credentials are entered, it’s often too late—and most organizations never saw it coming. To effectively mitigate these threats, security needs to shift to where the risk materializes: the browser. It’s time to stop phishing at the root source, not just at the perimeter.
To understand how these chained phishing sequences work, and how to detect and stop them before damage is done, watch Keep Aware’s latest on-demand webinar:
ChainLink Phishing: The Chained Sequences of Modern Phishing
Sponsored and written by Keep Aware.