A Stealth Upgrade: AMOS Now Comes with Full Remote Access
Security researchers have discovered a dangerous new version of the Atomic macOS Stealer (AMOS) that includes a built-in backdoor, allowing attackers to maintain persistent access to infected Apple devices.
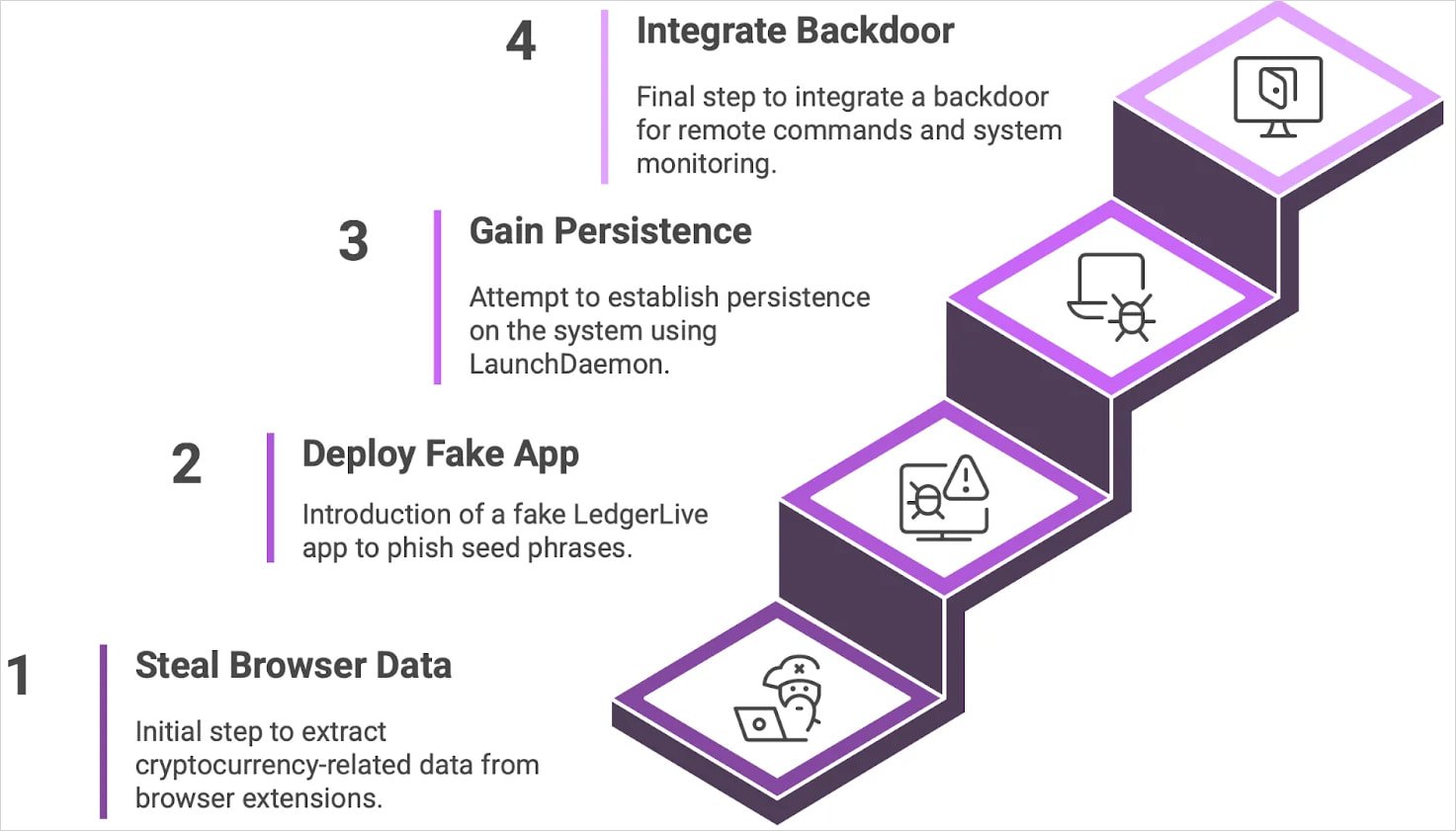
The malware, which already targeted sensitive user data like browser credentials and crypto wallets, now enables attackers to execute remote commands, survive system reboots, and retain control indefinitely.
Global Spread Confirmed by Analysts
The discovery was made by Moonlock, the cybersecurity division of MacPaw, following a tip from independent malware analyst g0njxa, who specializes in monitoring infostealers. Moonlock’s findings reveal that AMOS campaigns have already spread to over 120 countries, with the U.S., U.K., France, Italy, and Canada being among the most impacted.
“The backdoored version of Atomic macOS Stealer now has the potential to gain full access to thousands of Mac devices worldwide,” warned Moonlock researchers.
Circulation of unique Atomic stealer samples
Source: Moonlock
A Timeline of Evolving Threats
From Info-Stealer to Persistent Threat
Atomic Stealer first appeared in April 2023 as a malware-as-a-service (MaaS) tool marketed on Telegram for $1,000/month. Its original purpose was to harvest macOS files, credentials, and crypto extensions.
By November 2023, AMOS was used to expand the ClearFake campaign to macOS, and in September 2024, it was deployed by the Marko Polo cybercrime group in large-scale attacks. Most recently, attackers shifted from broad cracked software campaigns to more targeted phishing, luring cryptocurrency users and freelancers with job interviews.
Moonlock reports that the latest version includes:
- A stealthy backdoor component
- LaunchDaemon-based persistence
- Victim ID tracking
- A revamped command-and-control (C2) infrastructure
 Evolution of the Atomic stealer
Evolution of the Atomic stealer
Source: Moonlock