UK-based telecommunications company Colt Technology Services confirms that customer documentation was stolen as Warlock ransomware gang auctions files.
The British telecommunications and network services provider previously disclosed it suffered an attack on August 12, but this is the first time they confirmed data had been stolen.
“A criminal group has accessed certain files from our systems that may contain information related to our customers and posted the document titles on the dark web,” reads an updated security incident advisory on Colt’s site.
“We understand that this is concerning for you.”
“Customers are able to request a list of filenames posted on the dark web from the dedicated call centre.”
This statement comes after the Warlock Group began selling on the Ramp cybercrime forum what they claim is 1 million documents stolen from Colt. The documents are being sold for $200,000 and allegedly contain financial information, network architecture data, and customer information.
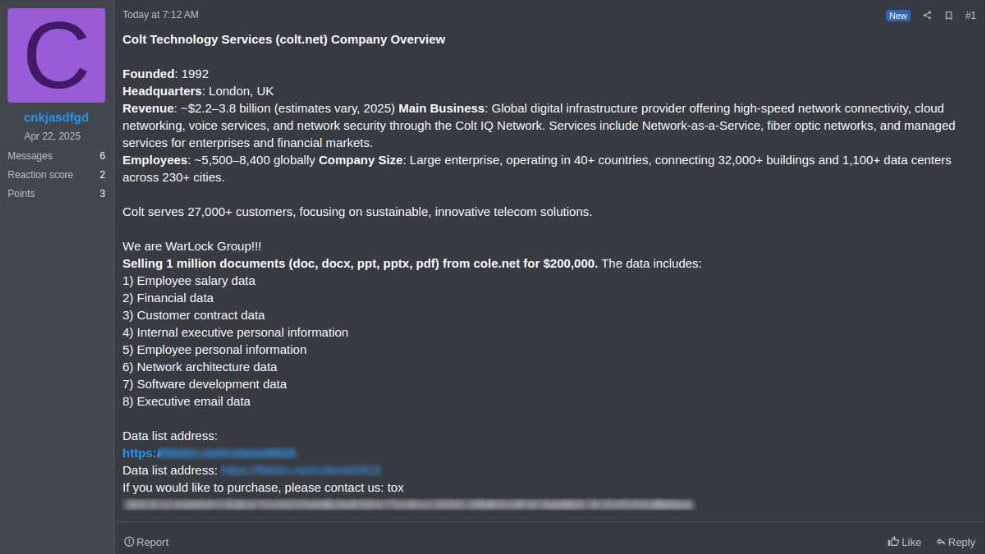
Source: KELA
BleepingComputer can confirm that the Tox ID listed in the forum post matches an ID used in earlier versions of the ransomware gang’s ransom notes.
The Warlock Group (aka Storm-2603) is a ransomware gang attributed to Chinese threat actors who utilize the leaked LockBit Windows and Babuk VMware ESXi encryptors in attacks.
When the ransomware gang launched in March 2025, they used LockBit ransomware notes in their attacks, customized to include a Tox ID for ransom negotiations.
In June, the ransomware gang branded itself as the “Warlock Group,” with customized ransom notes and dark web negotiation and data leak sites.
Last month, Microsoft reported that the threat actors were exploiting a SharePoint vulnerability to breach corporate networks and deploy ransomware.
In negotiations seen by BleepingComputer, the ransomware gang demands ransom ranging between $450,000 and millions of dollars.
