Security leaders today are rethinking email security, not because traditional methods have failed outright, but because the threat landscape and business needs have evolved beyond what legacy approaches can handle.
A surprising but apt analogy keeps surfacing: email security is stuck where antivirus (AV) was a decade ago, and it’s time it evolved like AV did, into an element of EDR.
The comparison might not be obvious at first. After all, email and endpoints seem like apples and oranges.
But when you look deeper, especially at the way EDR (Endpoint Detection and Response) grew from the core of AV, the parallel becomes impossible to ignore. Understanding that evolution offers a roadmap for what’s next in email security.
AV to EDR: A Lesson in Resilience
For years, legacy AV promised total protection. The goal was to detect and block every malicious file. If a file looked good, it was allowed. If it matched a known signature of badness, it was blocked. This binary “yes or no” model worked, until it didn’t.
Attackers adapted. Malware became polymorphic. New threats emerged faster than vendors could write signatures. Eventually, the industry had to admit an uncomfortable truth: 100% prevention is impossible.
That’s when EDR entered the scene. Rather than trying to replace AV entirely, EDR surrounded it, adding visibility, detection of suspicious behavior, forensic capabilities, and remediation tools.
Crucially, it introduced resilience into the security stack. Even if something slipped past AV, EDR was there to catch it later, investigate it, and limit its damage.
The endpoint had become a critical access point for attackers. Protecting it meant going beyond prevention, it required detection, response, and hardening.
Email Security: Caught in the Same Trap
Now look at email security today.
Most organizations still rely heavily on secure email gateways (SEGs) or built-in spam/phishing filters from providers like Google and Microsoft.
These tools are the AVs of email: they inspect inbound traffic, block the known-bad, and let the rest through. They’re great… until they’re not.
Phishing still happens. Business Email Compromise (BEC) is more sophisticated than ever. OAuth token abuse, insider threats, and hijacked accounts bypass traditional controls entirely. Like with AV, we’ve hit the limits of “prevent everything”.
And like with endpoints, email is a powerful pivot point. A compromised inbox gives attackers access to sensitive files, apps, and downstream workflows—think password resets, invoice fraud, or cloud file access.
The lesson from EDR applies perfectly: prevention alone isn’t enough. We need to invest in post-prevention controls, the “EDR for email” layer.
Our Data Shows Sensitive Files Grew 1100%: Insights from Securing Email & Drive.
Material Security’s analysis of email and cloud data uncovered surprising trends in how sensitive information is stored, shared, and secured, offering fresh perspective on evolving risks and defenses.
What EDR for Email Looks Like
This isn’t theoretical. It’s already happening.
At Material Security, we’ve taken an inside-out approach. Instead of starting with spam filtering or malicious link detection, we began with post-breach protections, tools that limit the impact after an attacker gets in.
Here’s what that includes and the questions that get answered when security goes beyond an email mindset:
- Visibility: Who accessed which emails? When? From where? Visibility is foundational to understanding incidents.
- Incident Response: Can you retroactively revoke access to sensitive content if an account is compromised?
- Granular Access Controls: Can you lock down emails with sensitive content like financials or PII, even for internal users?
- Retention Policies: Are you keeping emails longer than needed, increasing your blast radius?
- Identity Hardening: Are OAuth connections and email-based app signups tightly governed?
These aren’t replacements for existing email filters. They’re supplementary and necessary functions for stopping a breach in its tracks. And just like EDR made AVsmarter, evolving past the perimeter functions of email security makes it more powerful.
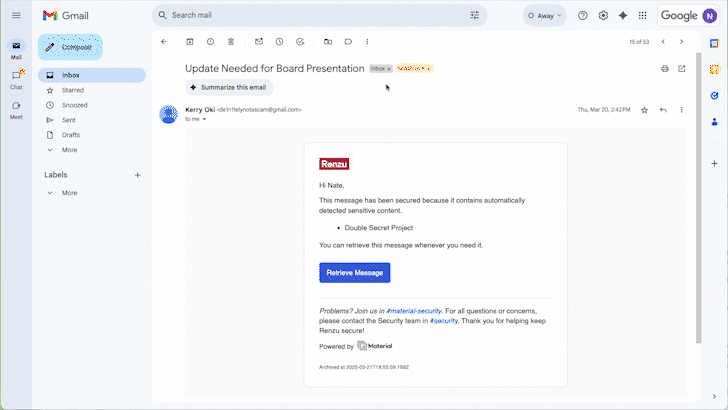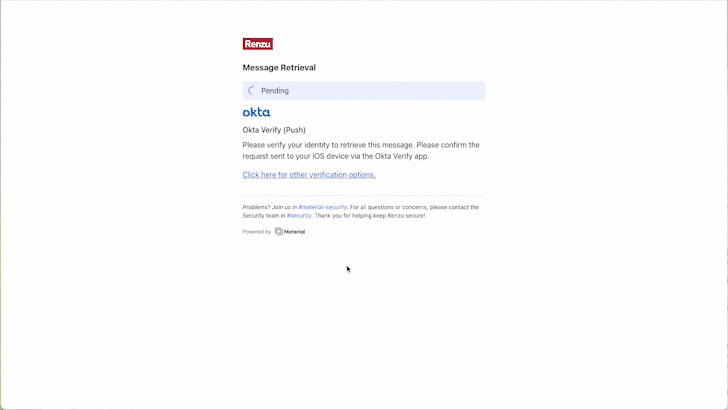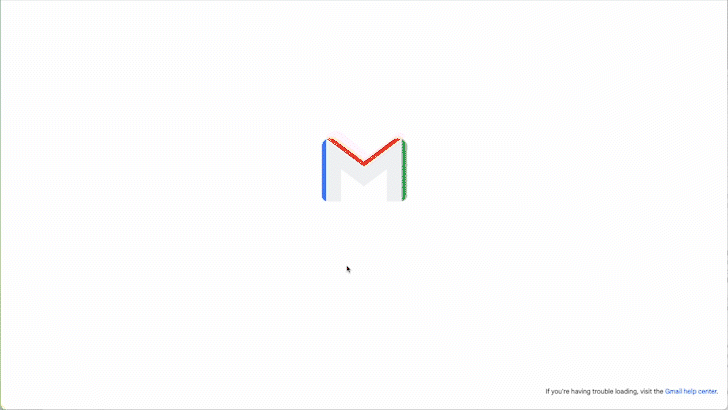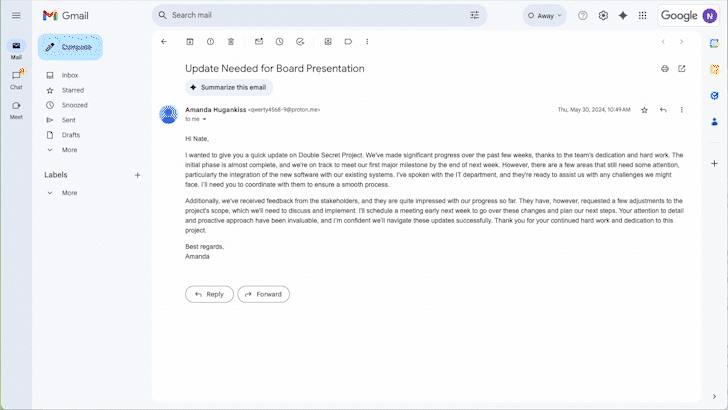
A Broader Security Shift
It’s not just about email anymore. As organizations rely more on Microsoft 365 and Google Workspace, the blast radius of an email account breach has widened. Attackers move laterally from inboxes into calendars, cloud storage, spreadsheets, and collaborative docs.
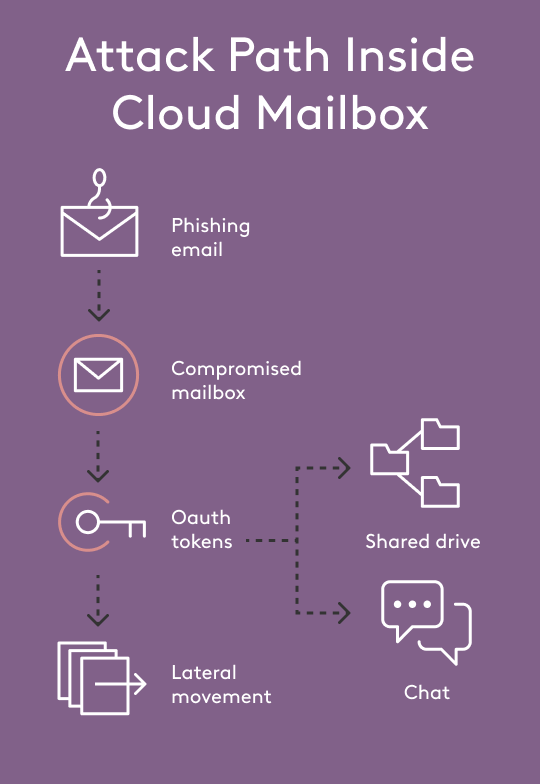
So the “EDR mindset” becomes all about expanding the work of security beyond email. Security should extend across the SaaS suite.
Material Security has already started down this path, bringing the same visibility, access controls, and threat response to the rest of the productivity ecosystem.
That’s why we believe standalone email security is reaching the end of its road. It’s no longer enough to build bigger spam traps. We need integrated, layered defenses across the tools that power work.
Time to Shift the Mental Model
For security teams, this shift requires a mindset change:
- From binary prevention → to layered resilience
- From perimeter inspection → to post-compromise visibility and control
- From point tools → to integrated security architecture
AV didn’t vanish when EDR arrived. It found its rightful place as part of a broader strategy. Email filtering will do the same. But organizations that fail to modernize risk being left with a brittle, prevention-only defense that no longer reflects how attackers work or how businesses operate.
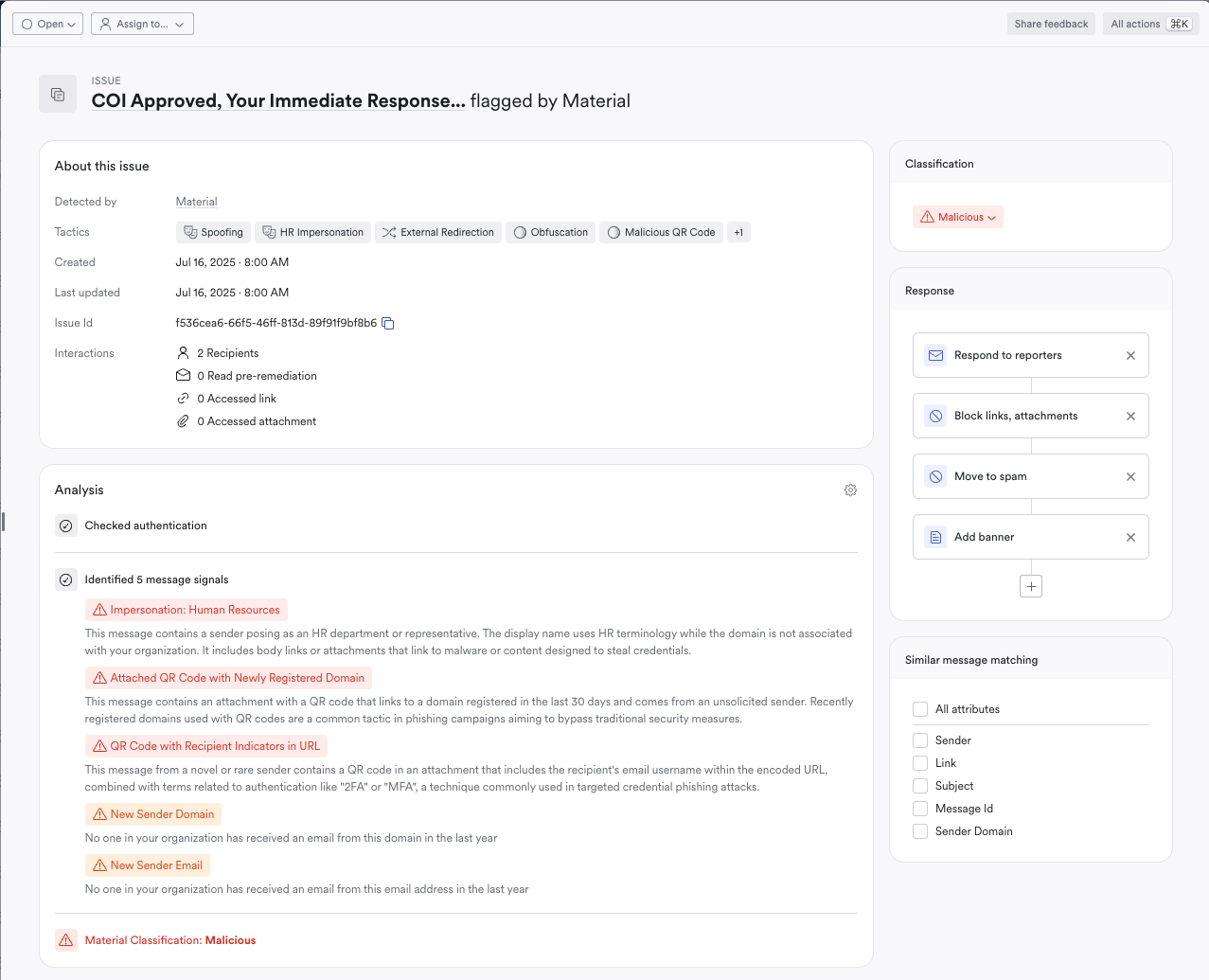
Just as EDR reshaped endpoint protection, we believe the next evolution of email security is already underway. The question isn’t if it will happen. It’s whether you’ll be ahead of the curve or playing catch-up after the next breach.
Want to see what EDR for email looks like in action?
Learn more about Material Security’s approach and see purpose-built cloud workspace security in action.
Sponsored and written by Material Security.