Introducing SharpInvisibleProxy
Once thing that can interfere with exploitation attempt, is if the client validate that the endpoint is exist on the server before submitting the credentials. To overcome this, we can use Invisible proxy (instead of HTTPS web server) which access to original server and fetch the required data.
To facilitate this type of attacks, the author developed SharpInvisibleProxy which is a C# invisible proxy tool. Once configured, the tool spawns a web service presenting the configured certificate, and write to the console the requests intercepted.
Extract credentials from HTTP traffic
My Network, My Rules!
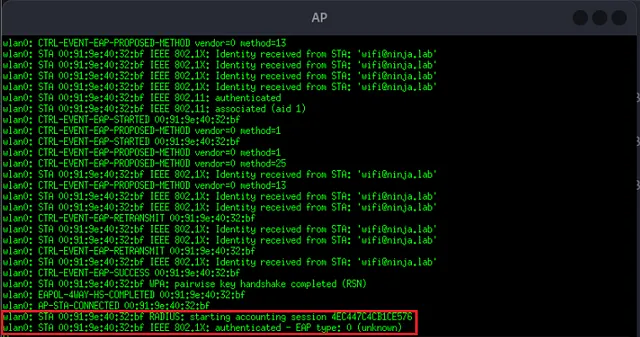
Another potential attack vector to consider is wireless networks, which have become less prevalent due to the adoption of 802.1x authentication. This protocol leverages certificates for authentication rather than traditional username-password methods. However, given the capabilities of Server Authentication certificates, this vector warrants reevaluation.
An attacker could exploit this by deploying a rogue access point and executing an Evil Twin attack. This method could be effective even if clients are configured to validate the server’s identity, as the attacker could present a trusted certificate. Consequently, the attacker would gain network access to client machines, bypass network segmentation, and intercept or manipulate client traffic, as the network is under the attacker’s control.
In the example below, the author utilized the default WebServer certificate template (which, by default, enables Server Authentication and includes a supplied subject) in his lab to successfully execute an Evil Twin attack. This allowed him to authenticate clients to my rogue network instead of the legitimate one.
client trust the AP certificate and connected to malicious AP
the client refuse to connect to the AP because of untrusted certificate
Combining this attack with a proxy-based approach creates a highly effective method. Using these two techniques, an attacker can leverage an extracted certificate to deploy a rogue access point that clients automatically connect to. The attacker can then use a Server Authentication certificate, alongside protocols like DNS, to control and intercept client data. This, in turn, provides an easier pathway back into the corporate network by intercepting VPN connections, including MFA claims.
Code Execution? We can Manage to!
The path to executing code using Server Authentication certificates begins by exploring common solutions with code execution capabilities within typical network environments. The most obvious candidates are client management and software distribution platforms, which often rely on the HTTP protocol for client-server communication.
One such example is ManageEngine Endpoint Central, a product that enables IT teams to centrally manage, deploy, and update software packages across all workstations in an organization.
According to ManageEngine’s best practices, it is recommended to replace the default server certificate with one issued by the organization and trusted by clients typically through the internal Active Directory Certificate Authority (CA). During testing, the author observed that while the client does validate the server’s certificate, it does not validate the certificate’s serial number. This was a promising discovery, as it satisfies the first condition necessary for the attack.
At this stage, it becomes possible to extract a Server Authentication certificate using the hostname of the ManageEngine UEM server. As a result, clients will trust this forged certificate, opening the door for potential code execution.
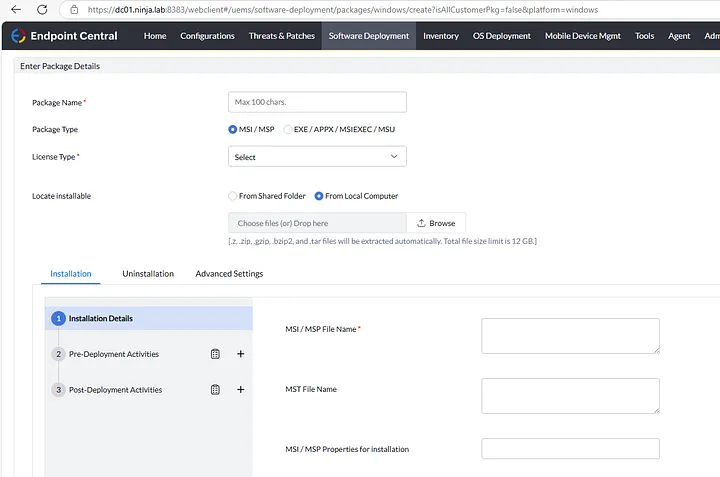
In ManageEngine Endpoint Central, software is distributed as “Packages,” where the administrator is required to provide installation files such as EXE or MSI.
Package creation page in UEM admin panel
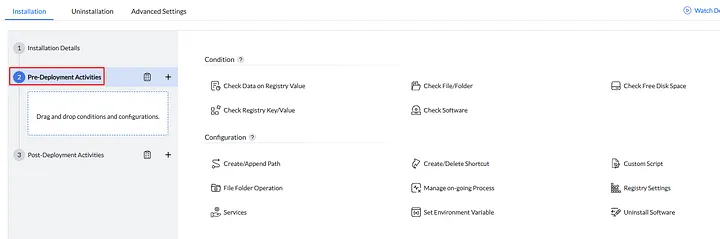
Interestingly, in addition to the main installation file, there are Pre-Deployment and Post-Deployment sections that allow administrators to perform actions before and after the installation process.
Pre-deployment script
There are several options to choose from; however, in this case, the “Custom Script” option seems to be the most suitable.
UEM allows for uploading script files, as well as providing command-line options:
The author created a package with a command-line pre-deployment task and tested it on an agent.
A package configured with a command line
Deploy the package on a client
Monitoring the process on the agent machine reveals that the command was executed with SYSTEM-level privileges:
PowerShell process executes by the task
However, checking the proxy reveals that the command line is encrypted, making it impossible to modify.
Server response with the encrypted command line