A large-scale phishing campaign has targeted nearly 12,000 GitHub repositories, tricking developers into granting full access to their accounts and code. The attack, which is still ongoing, involves fake “Security Alert” issues warning of unauthorized login attempts.
Fake security alert issues created in GitHub repositories
Source: BleepingComputer
How the Scam Works
The phishing messages, posted as GitHub issues, claim that there was a suspicious login attempt from Reykjavik, Iceland (IP: 53.253.117.8). The message urges users to take immediate action by updating their password, reviewing active sessions, and enabling two-factor authentication (2FA).
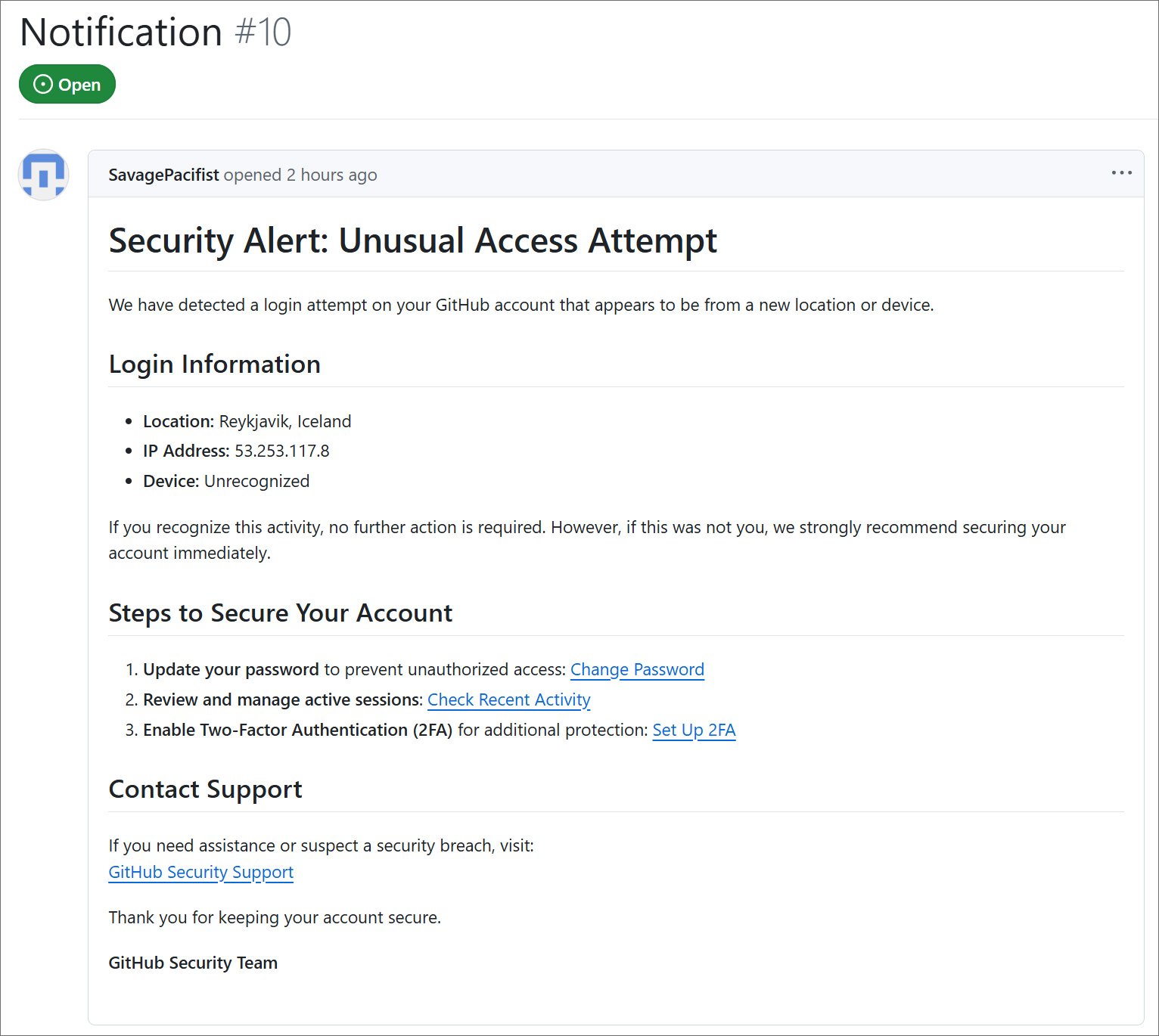 Fake “Security Alert” issue posted to GitHub repositories
Fake “Security Alert” issue posted to GitHub repositories
Source: BleepingComputer
However, all the provided links redirect to a GitHub authorization page for a malicious OAuth app named “gitsecurityapp”. If a user unknowingly grants access, the attackers gain full control over their repositories, user data, workflows, and even the ability to delete repositories.
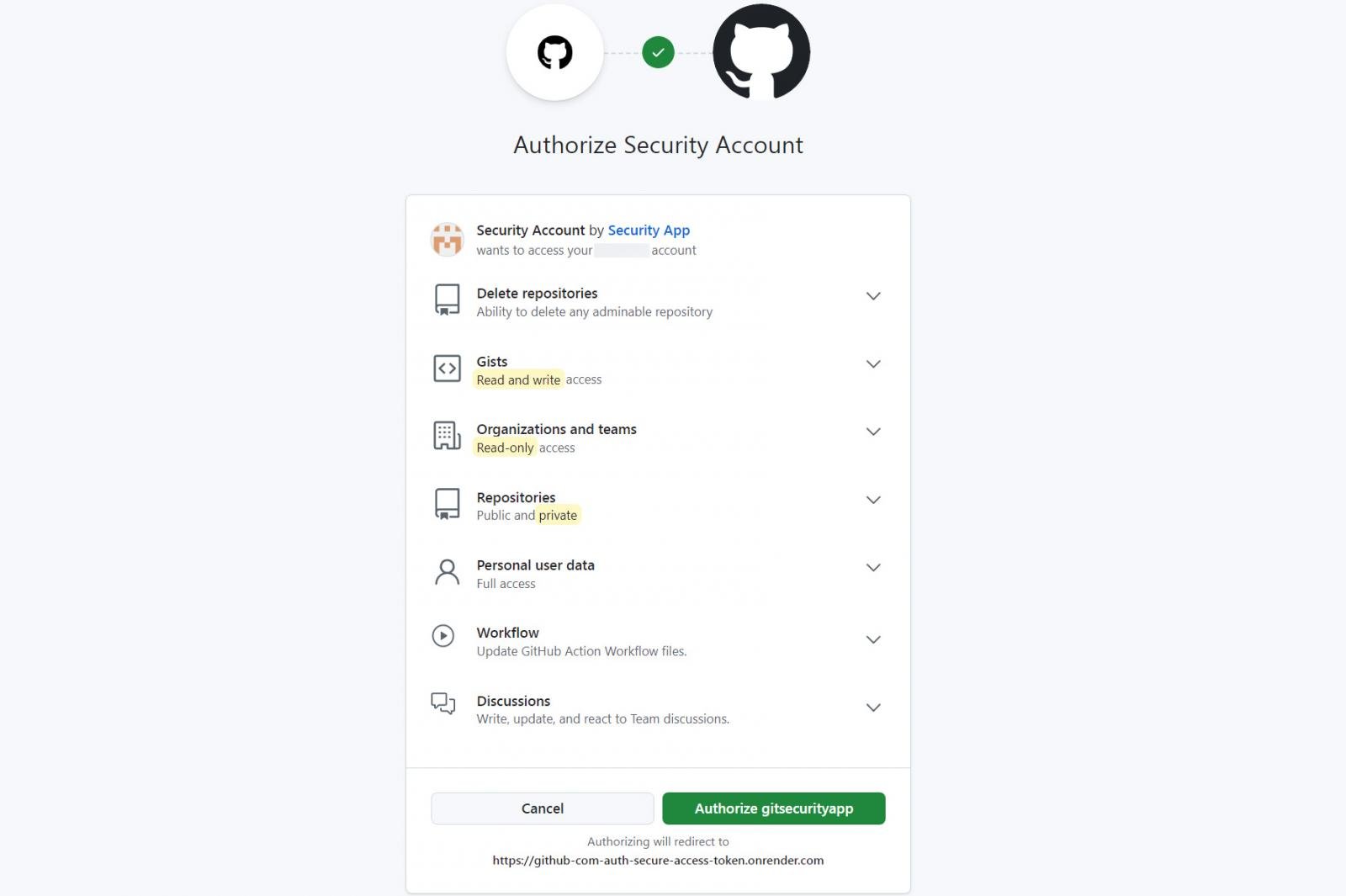 Permissions requested by malicious OAuth app
Permissions requested by malicious OAuth app
Source: BleepingComputer
Dangerous Permissions Requested
The malicious OAuth app requests extensive permissions, including:
- Full access to public and private repositories (repo)
- Read and write access to user profiles (user)
- Control over GitHub Actions workflows (write:workflow)
- Ability to delete repositories (delete_repo)
- Read organization memberships and projects (read:org)
Once authorized, the app sends an access token to a callback URL hosted on onrender.com (Render), allowing attackers to remotely control the compromised account.