For years, Data Loss Prevention (DLP) solutions focused on email, endpoints, and network traffic, where security teams could enforce clear policies with predictable outcomes.
But work has changed. Employees aren’t just moving data through controlled corporate channels anymore—they’re copying, pasting, uploading, and transferring sensitive information through the browser every day.
Inline DLP was never built to control how employees handle data inside SaaS applications. Personal and corporate accounts blur together while newly adopted Gen-AI tools and browser extensions quietly expand the risk surface.
The browser is now the largest data exfiltration point, yet security strategies remain stuck in a perimeter-based world. The real challenge isn’t just detecting data loss; it’s understanding why traditional defenses keep missing it.
How Data Loss Happens in the Browser
Data exfiltration no longer happens through obvious channels like USB drives or unauthorized email attachments. Instead, employees unknowingly expose data as they work in the web browser.
A developer pastes API keys into ChatGPT, exposing credentials. A sales rep exports CRM contacts to a personal Google Sheet, revealing confidential customer data. A marketing manager grants OAuth permissions to an AI tool, unknowingly allowing ongoing data access.
While not blatant security violations, these routine actions bypass controls because the data never officially leaves an approved app. The browser is now the main channel for this data movement with employees uploading, copying, and transferring sensitive information across several SaaS applications, each handling data differently.
This growing usage of applications has made enforcing consistent DLP policies increasingly complex.
- Data exposure goes beyond uploads: Sensitive data now moves beyond file transfers, with copy-paste actions, browser extensions, and Gen-AI prompts enabling data exposure.
- Cloud storage obfuscates data movement: Many SaaS providers leverage AWS, Azure, or GCP for backend storage and signed requests, making it difficult to trace uploads back to specific applications.
- Data sprawl across browsers: Employees use Chrome, Edge, Firefox, and Safari, each creating monitoring blind spots for security teams.
To better understand where data is going, we have analyzed the top shared storage destinations across browsers, revealing how most activity is a blend of personal and work behavior.
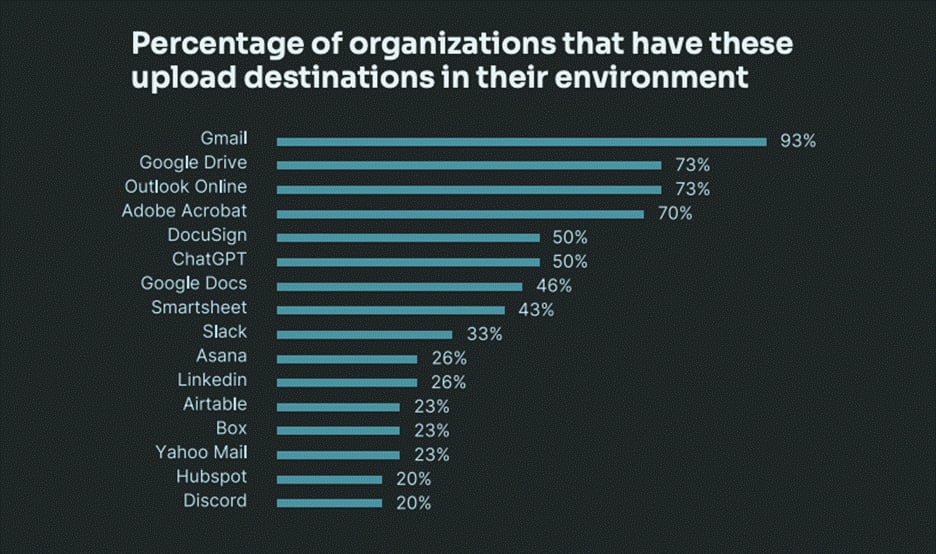
1. The Hidden Risk of Personal Accounts
Personal accounts are one of the most overlooked and significant sources of data loss. Employees regularly switch between work and personal accounts within the same browser session, especially in Google Workspace, Microsoft 365, ChatGPT, and Dropbox, blurring the line between corporate and unmanaged environments.
In our recent State of Browser Security report, we highlight the scale of this risk:
- 39% of all browser activity on Google web apps involves personal accounts.
- 34% of upload events on managed devices go to personal accounts.
Employees aren’t typically acting maliciously, but it’s easy for resumes, tax forms, and personal information to creep into daily work on corporate devices, often through personal cloud storage, email, or messaging apps.
Without browser-based policies, security teams have no control over whether data is moving to an approved business account or an unmanaged personal one.
Blocking all personal uploads is neither practical nor effective. Instead, organizations need browser-enforced policies that differentiate between corporate and personal usage, ensuring data stays within sanctioned environments without disrupting legitimate work.
Keep Aware provides security teams with instant visibility into browser activity. With click-by-click telemetry, DOM-tree analysis, and threat blocking capabilities, you can detect and stop malicious activity where it starts. Gain full investigative power and ensure browser threats are stopped before they harm your users, data, or apps.
2. Data in Motion is Most at Risk
Organizations are rapidly adopting data classification and labeling to manage sensitive information. Tools like Microsoft Purview have expanded classification efforts, but these solutions focus primarily on data at rest, leaving a major enforcement gap when data is in motion.
Identifying sensitive data is only half the battle; securing it as it moves through SaaS applications, browsers, and collaboration tools is the real challenge.
Unsurprisingly, most data loss happens when information is actively handled, shared, or transferred. The same SaaS apps that drive productivity also introduce high-risk data exposure:
- Google Drive and Gmail store business documents—but also personal tax forms.
- Slack enables team discussions—but also unauthorized file sharing.
- ChatGPT summarizes reports—but can just as easily ingest confidential contracts.
Traditional security models assume that blocking known exfiltration channels is enough. Yet when the most commonly used business apps are the most common sources of data loss, relying on static controls no longer works. Organizations need real-time enforcement at the browser level to secure data in motion, ensuring that sensitive information remains protected without disrupting productivity.
3. Extensions and Shadow IT: A Hidden Backdoor
Beyond direct data exfiltration, browser extensions and shadow IT services create another major security gap. Employees install plugins and grant permissions to apps every day often without realizing how much access they are giving away.
- Malicious Extensions: Attackers use extensions to siphon data, capture keystrokes, and extract authentication tokens.
- Consent Phishing: Employees are tricked into granting excessive OAuth permissions, allowing continuous data access even after they log out.
- Third-Party Integrations: AI tools, note-taking apps, and automation services often request broad data permissions that security teams can’t easily monitor.
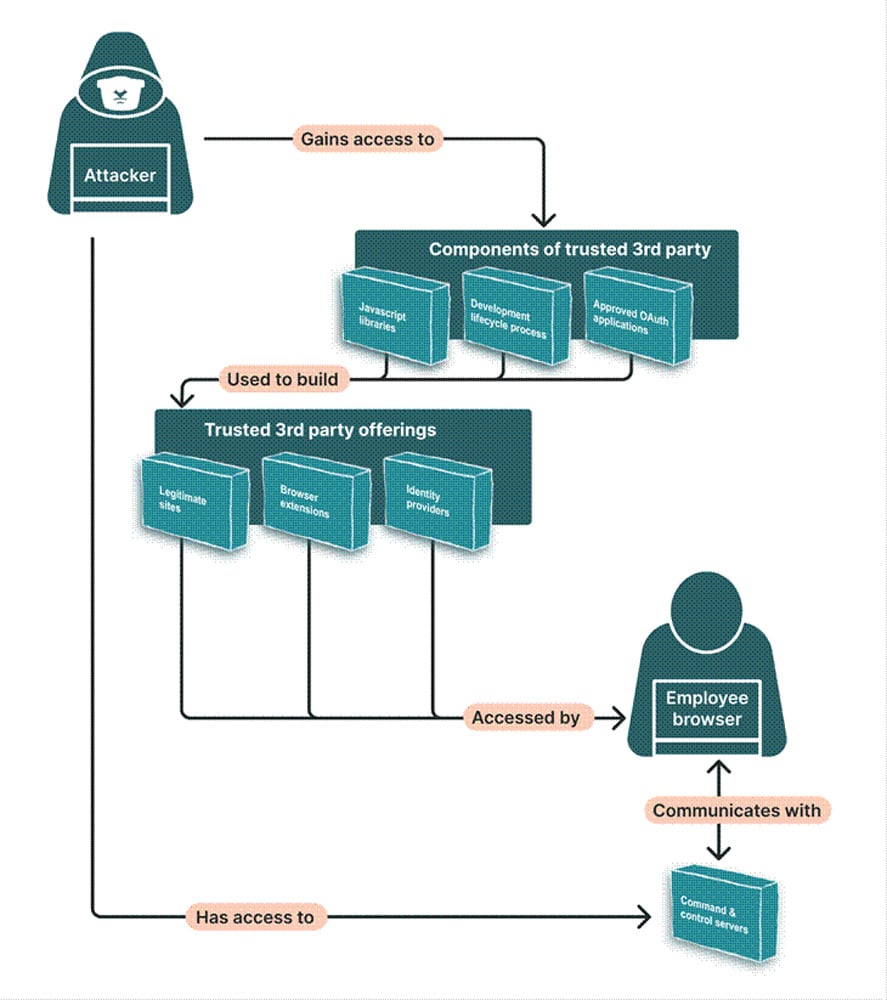
The Browser is the New Security Perimeter
The browser has become the most critical yet overlooked layer of enterprise security. Existing controls were built for email and endpoints, not modern work where everything is handled through the browser. Real-time detection and response in the browser is no longer optional.
Security teams need visibility inside applications, not just where data is going. Blocking exfiltration isn’t enough and proactive protection must happen at the source.
A browser-based DLP model ensures security follows the data, applying consistent protection without disrupting work. Interested in learning more?
Request a free demo with a Keep Aware team member to learn more about implementing browser security in your organization.
AUTHOR: Ryan Boerner
Boerner, a computer engineer turned cyber security practitioner, began as a SOC analyst tackling network threats across Texas agencies. Specializing in network and email security, he later honed his expertise at IBM and Darktrace, working with organizations of all sizes. Seeing a critical gap between security teams and employees—where strong defenses still let threats through—he founded Keep Aware to make the browser a cornerstone of enterprise security.
Sponsored and written by Keep Aware.