An Android malware app called SpyLend has been downloaded over 100,000 times from Google Play, where it masqueraded as a financial tool but became a predatory loan app for those in India.
The app falls under a group of malicious Android applications called “SpyLoan,” which pretend to be legitimate financial tools or loan services but instead steal data from devices for use in predatory lending.
These apps lure users with promises of quick and easy loans, often requiring little documentation and offering attractive terms. However, upon installation, they request excessive permissions, allowing the apps to steal personal data such as contacts, call logs, SMS messages, photos, and device location.
This harvested information is then exploited to harass, extort, and blackmail users, especially if they fail to meet the app’s repayment terms.
Loan scams and extortion
Cybersecurity firm CYFIRMA has discovered an Android app named “Finance Simplified” that claims to be a financial management application and has amassed 100,000 downloads on Google Play.
However, CYFIRMA states that the app displays more malicious behavior in certain countries, like India, where it steals data from user’s devices to be used in predatory lending. The researchers say they also discovered additional malicious APKs that appear to be variants of the same malware campaign, namely KreditApple, PokketMe, and StashFur.
Although the app has now been removed from Google Play, it may continue to run in the background, collecting sensitive information from infected devices.

Source: BleepingComputer
Multiple user reviews for Finance Simplified on Google Play show that the app offers lending services that attempt to extort borrowers if they don’t pay high interest rates.
“Very very very bad app they given low loan amount nd black mail to pay High otherwise photoes edited as a nude nd black mailing,” reads a user review for the now-pulled app.
The apps also claim to be registered Non-Banking Financial Companies (NBFCs), which CYFIRMA says is untrue.
To evade detection on Google Play, Finance Simplified loads a WebView to redirect users to an external website from where they download a loan app APK hosted on an Amazon EC2 server.
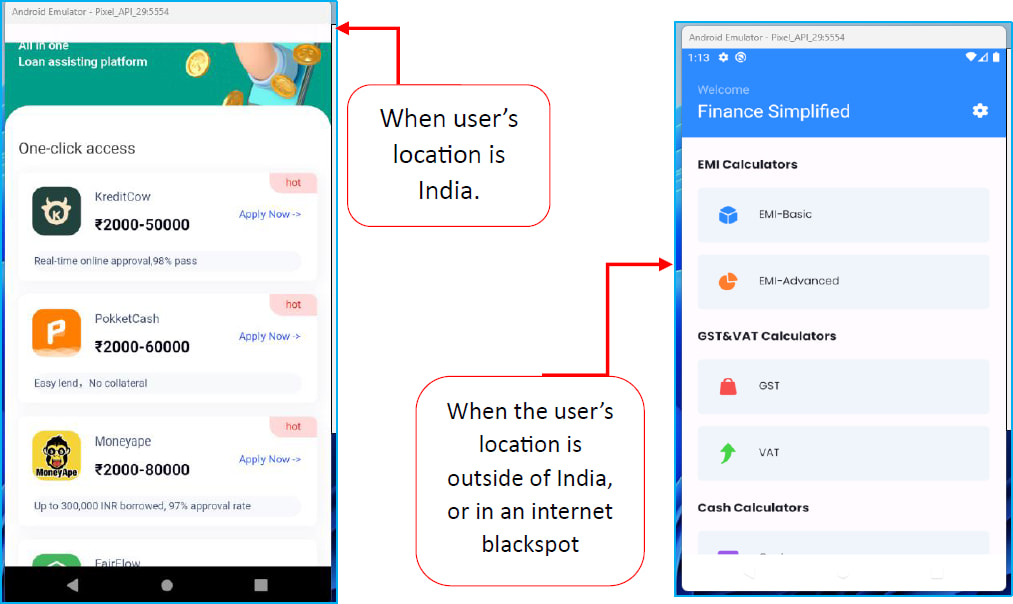
“The Finance Simplified app appears to target Indian users specifically by displaying and recommending loan applications, loading a WebView that shows a loan service that redirects to an external website where a separate loan APK file is downloaded,” explains CYFIRMA.
The researchers discovered that the app will only load the deceptive interface if the user location is India, which shows the campaign has a specific targeting.
Source: CYFIRMA
Sensitive data stolen by app
The more worrying aspect of the malware’s activity is the data collection, which includes sensitive personal information stored on the user’s device.
Here’s a summary of the data the malware steals:
- Contacts, call logs, SMS messages, and device details.
- Photos, videos, and documents from internal and external storage.
- Live location tracking (updated every 3 seconds), historical location data, and IP address.
- Last 20 text entries copied to the clipboard.
- Loan history and banking SMS transaction messages.
Although that data is primarily used for extorting the victims who made the mistake of applying for a loan, it may also be used for financial fraud or resold to cybercriminals for profit.
.jpg)
Source: CYFIRMA
If you suspect your device was infected by any of the mentioned apps or similar, remove them immediately, reset permissions, change banking account passwords, and perform a device scan.
Google’s Play Protect tool detects and blocks known malware and predatory apps, so ensure it’s active on your device.