A help desk phishing campaign targets an organization’s Microsoft Active Directory Federation Services (ADFS) using spoofed login pages to steal credentials and bypass multi-factor authentication (MFA) protections.
The targets of this campaign, according to Abnormal Security that discovered it, are primarily education, healthcare, and government organizations, with the attack targeting at least 150 targets.
These attacks aim to gain access to corporate email accounts to send emails to additional victims within the organization or perform financially motivated attacks like business email compromise (BEC), where payments are diverted to the threat actors’ accounts.
Spoofing Microsoft Active Directory Federation Services
Microsoft Active Directory Federation Services (ADFS) is an authentication system that allows users to log in once and access multiple applications and services without having to enter their credentials repeatedly.
It is typically used in large organizations to provide single sign-on (SSO) across internal and cloud-based applications.
The attackers send emails to targets impersonating their company’s IT team, asking them to log in to update their security settings or accept new policies.
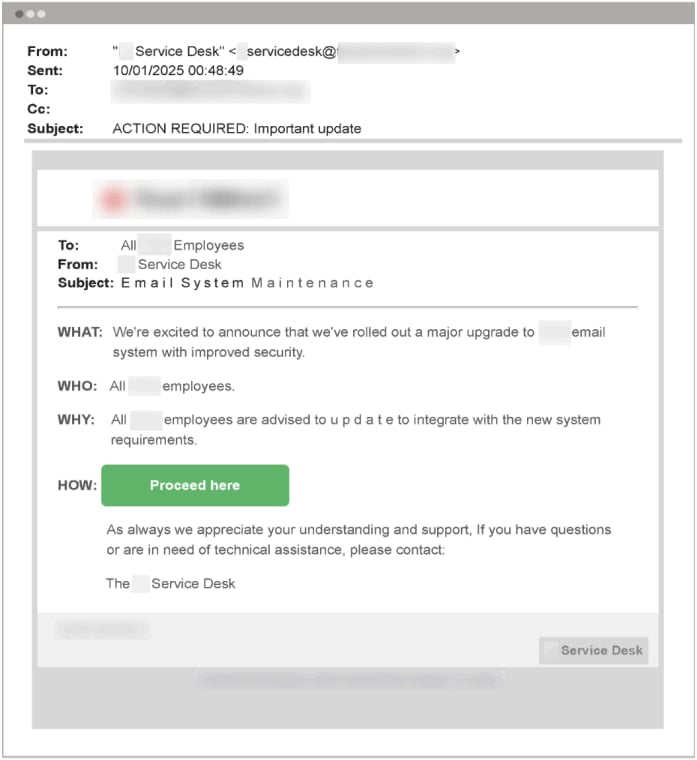
Source: Abnormal Security
Clicking on the embedded button takes victims to a phishing site that looks exactly like their organization’s real ADFS login page.
The phishing page asks the victim to enter their username, password, and the MFA code or tricks them into approving the push notification.
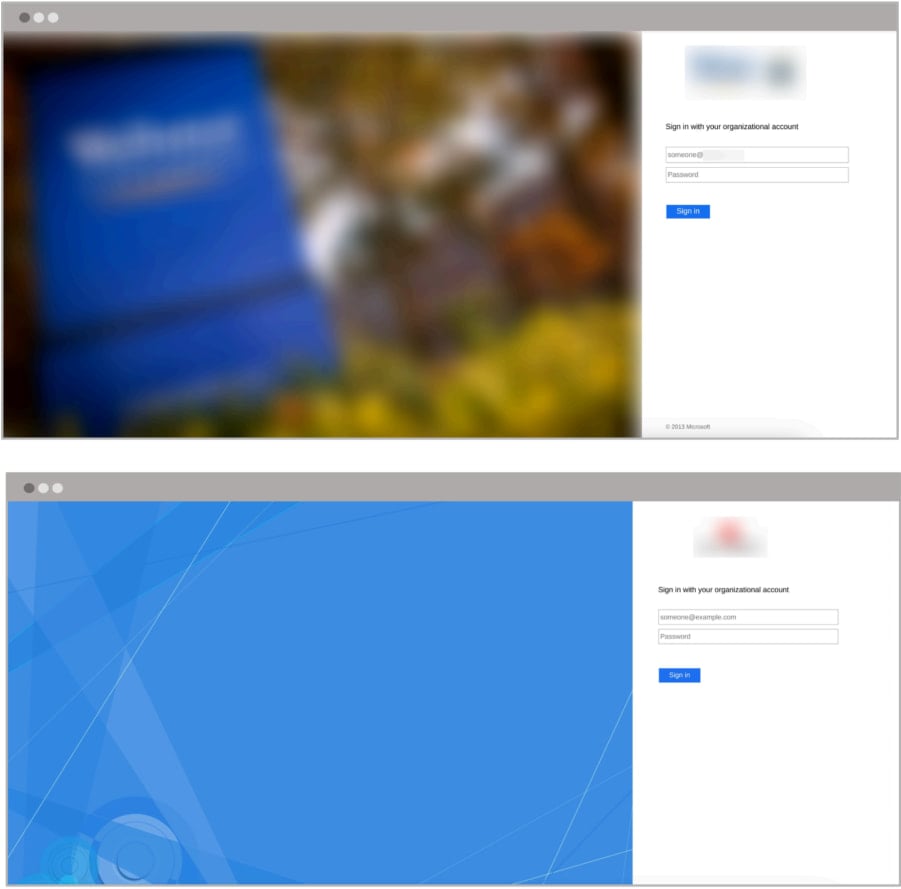
Source: Abnormal Security
“The phishing templates also include forms designed to capture the specific second factor required to authenticate the targets account, based on the organizations configured MFA settings,” reads Abnormal Security’s report.
“Abnormal observed templates targeting multiple commonly used MFA mechanisms, including Microsoft Authenticator, Duo Security, and SMS verification.”
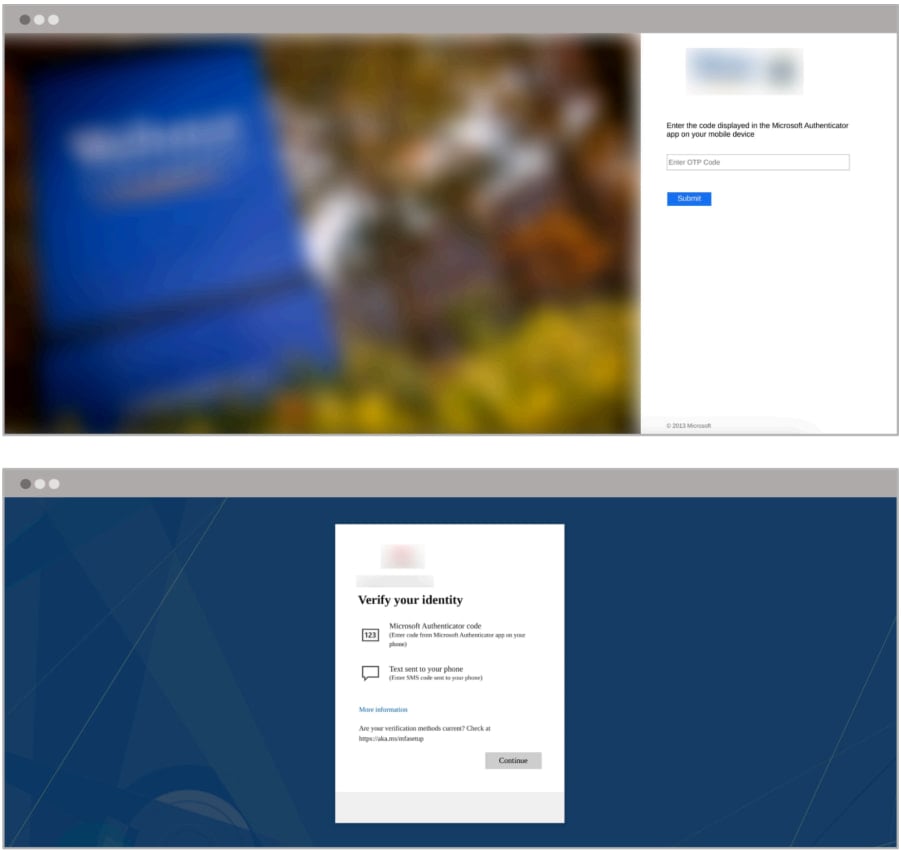
Source: Abnormal Security
Once the victim provides all the details, they are redirected to the legitimate sign-in page to reduce suspicion and make it appear as if the process has been successfully completed.
Meanwhile, the attackers immediately leverage the stolen information to log into the victim’s account, steal any valuable data, create new email filter rules, and attempt lateral phishing.
Abnormal says the attackers in this campaign used Private Internet Access VPN to obscure their location and assign an IP address with better proximity to the organization.
Even though these phishing attacks do not breach ADFS directly, and rather rely on social engineering to work, the tactic is still notable for its potential effectiveness given the inherent trust many users have on familiar login workflows.
Abnormal suggests that organizations migrate to modern and more secure solutions like Microsoft Entra and introduce additional email filters and anomalous activity detection mechanisms to stop phishing attacks early.